
Make Every AWS VPC Packet Encrypted In Transit
You can't fix what you can't see. In the cloud, plaintext in transit is an invisible landmine. It can turn into a compliance mess fast.
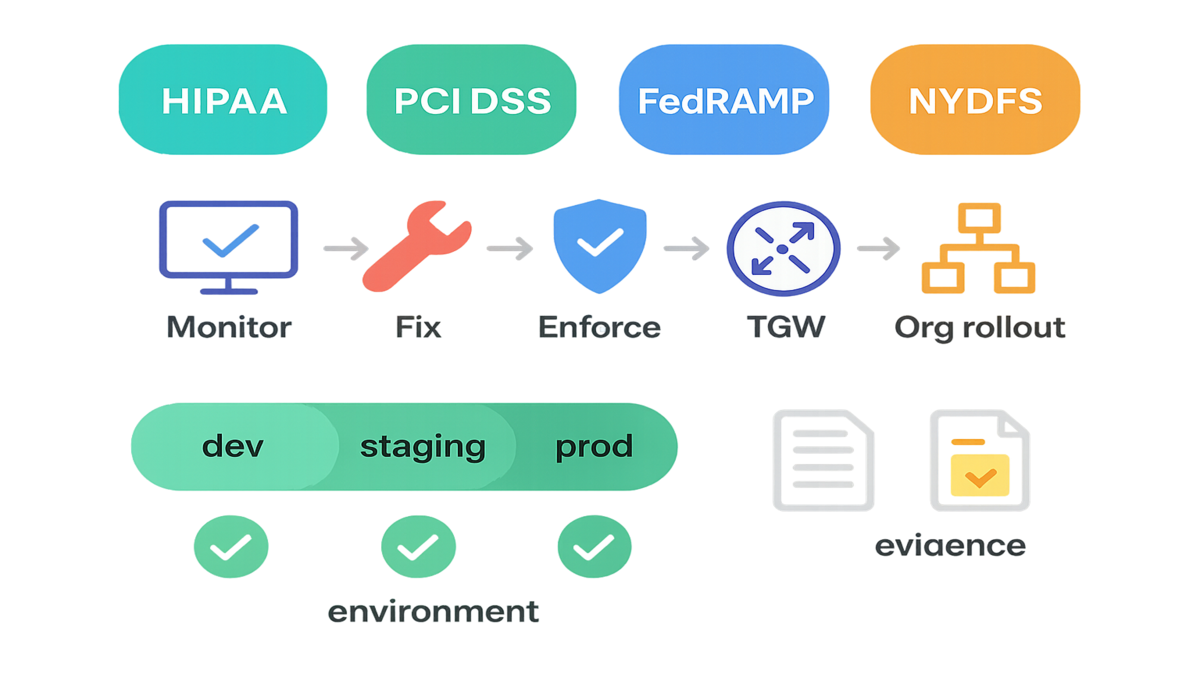
Here’s the good news: AWS just made it much harder to miss. VPC Encryption Controls give you one switch to watch and enforce encryption in transit across your VPCs, without duct-taping tons of service policies. Translation: less audit panic, more proof.
If you’ve ever tried to prove HIPAA or PCI DSS with screenshots and vibes, this flips things. You get flow logs with an encryption-status signal, a two-step rollout (monitor first, enforce later), and support that covers Nitro, Fargate, and Transit Gateway. You see who sends plaintext, you fix it, then you lock it down.
You want aws encryption in transit to be boring and automatic. This gets you there.
Think of it like seatbelts for your VPC. First you check who’s buckled (monitor). Then you tighten straps (remediate). Then you make buckling the default (enforce). Simple, repeatable, and visible. So when someone asks, 'Are we encrypted?', you can say 'Yes' and show receipts.
TLDR
- Turn on monitor mode to spot plaintext across VPCs before enforcing.
- Flow logs add encryption-status: Nitro, TLS at the app layer, or both.
- Enforce mode blocks features that allow unencrypted traffic.
- Works with Nitro, Fargate, ALB, and Transit Gateway (enable TGW separately).
- Map to HIPAA, PCI DSS, FedRAMP, and NYDFS for easier evidence and audits.
- For older instances, upgrade to supported types to keep traffic encrypted.

Kills plaintext by design
Monitor first then enforce
VPC Encryption Controls run in two gears:
- Monitor mode: You audit flows within and across VPCs and see where plaintext appears. This is your safety net. Fix issues before you flip the switch.
- Enforce mode: After validation, AWS blocks features or paths that allow unencrypted traffic inside the VPC boundary. For new VPCs, you can start here on day one.
A practical rollout looks like this: enable monitor on existing VPCs, watch the new encryption-status field in VPC Flow Logs, squash the plaintext hotspots, then upgrade to enforce. For greenfield VPCs, start with enforce to make vpc encryption in transit aws the default, not a wishlist.
Add a lightweight checklist and a change window. Your checklist can be as simple as: 1) turn on monitor, 2) confirm logs are flowing, 3) fix the top three plaintext paths, 4) run clean for 1–2 weeks across peak hours, 5) switch to enforce during a scheduled window with a rollback plan. This keeps the drama low and the signal high.
Want to avoid surprise app issues? Announce the plan to service owners ahead of time. Give them this note: if you see alerts for plaintext between these services, switch that HTTP call to HTTPS or enable mTLS. Most fixes are one-line config changes, not rewrites.
One control per VPC
Each VPC gets exactly one encryption control. You can tag the control for env, app, and owner. That is gold if you manage dozens of accounts. It helps you line up enforcement with blast-radius boundaries.
First-hand example: a healthcare team in a multi-account setup enabled monitor in dev, found an ALB listener exposing HTTP from a migration, switched to HTTPS with TLS 1.2+, validated zero plaintext for a week, then enforced across dev, stage, and prod in waves.
At scale, treat tagging as your map and your memory. Pick a simple scheme like: env=prod|stage|dev, system=payments|ehr|analytics, owner=email. With tags in place, you can query controls, prioritize fixes by critical systems, and prove scope to auditors. Bonus: those tags make dashboards and on-call handoffs much easier.
How the encryption happens
Nitro TLS or both signal
AWS enriches VPC Flow Logs with encryption-status to show if traffic is protected by:
- Nitro hardware encryption in transit, which is transparent link protection in AWS’s network fabric.
- Application-layer encryption such as TLS, like HTTPS, database TLS, or mTLS for services.
- Or both, giving you defense in depth.
This matters because encrypted isn’t one thing. Nitro-level protection reduces plaintext exposure inside AWS’s infrastructure. App-layer TLS gives you end-to-end crypto and identity. You’ll use the signal to prioritize fixes where neither protection exists.
Quick mental model:
- Nitro: fast, transparent, handled by hardware. Great for risk reduction inside AWS paths.
- TLS: visible to your app, terminates at known endpoints, gives identity, cipher control, and audits.
- Both: the happy place, defense in depth with speed and certainty.
VPC Flow Logs don’t capture payloads; they capture metadata. That’s good for privacy and scale. Here, the key metadata is was this flow protected? You can spot weak links without packet sniffers or inline proxies.
Beyond EC2 Fargate ALB
This isn’t limited to EC2 Nitro instances. The enforcement model extends to Fargate tasks, Application Load Balancers, and AWS Transit Gateway. The catch: if your VPCs route through Transit Gateway, you must enable encryption controls on the TGW to protect inter-VPC traffic end to end. Good news: turning it on doesn’t disrupt existing flows.
Got older instance types without native in-transit encryption? You’ll need to upgrade to supported generations to fully benefit. Until then, app-layer TLS is still a must.
Practical tip: verify every hop. ALB should terminate HTTPS, pass traffic to targets over HTTPS or mTLS, and your databases should require TLS from clients. If you use PrivateLink for cross-account access, keep TLS on as well. A private network plus an encrypted session is stronger than either alone.
The compliance unlock
Map controls to HIPAA
If you live in regulated land, this is your fast pass. Encryption in transit is table stakes across frameworks:
- HIPAA: Protect ePHI in transit with strong encryption and solid key management.
- PCI DSS: Encrypt cardholder data in transit over open networks and segment hard.
- FedRAMP: Enforce FIPS-validated algorithms and document your controls.
- NYDFS 500.15(a): Encrypt nonpublic information in transit over external networks.
VPC Encryption Controls give you centralized, authoritative enforcement and evidence. Instead of proving a negative, you produce flow logs and config states that show encryption-status over time.
Translate this to policy-speak: all connections between workloads, load balancers, databases, caches, and inter-VPC paths must be encrypted in transit. Deviations must be approved, time-bound, and tagged. Now you’ve got a crisp rule and a way to verify it.
Proving it to auditors
Make it mechanical:
- Evidence: flow logs with encryption-status trends, change tickets for fixes, and a record of the switch from monitor to enforce.
- Policy: a written requirement for all VPC traffic encrypted in transit with deviations tracked.
- Scope: include Transit Gateway, inter-VPC paths, and service-to-service flows like ALB and PrivateLink.
- Exceptions: time-bound, approved, and tagged. If you must allow plaintext in a lab VPC, document it and restrict egress.
A financial services team we worked with cut audit prep time by half. No sprawling screenshots. Just export flow-log slices, map to tickets, and attach a signed change record for the enforce switch.
Pro tip: build a recurring report. Each month, pull flows where encryption-status equals none, list affected services, show remediation dates, and include a sign-off. That single PDF answers three classic questions: what’s the rule, how do you monitor it, and what happens when it breaks?
The playbook
Pinpoint where plaintext leaks
Use monitor mode like a flashlight. Look for these encryption in transit examples of issues:
- ALB listener still serving HTTP because a legacy health check never moved.
- Internal service calls using HTTP between ECS or EKS microservices, not HTTPS or mTLS.
- RDS or client not enforcing TLS; apps quietly downgrade.
- Redis or ElastiCache without in-transit encryption enabled.
- Transit Gateway attached VPCs not covered, leaving an unencrypted interconnect path.
For each, you can test fixes in place and watch encryption-status turn green.
When you triage, start with systems touching sensitive data like payments, health, or PII. Then anything internet-facing. Then high-traffic internal services. Reduce the biggest risks first and build momentum.
Quick wins across popular services
- ALB: redirect HTTP to HTTPS, enforce TLS 1.2+, and use ACM for certs.
- S3: enforce HTTPS with a bucket policy using aws:SecureTransport = true. That covers encryption in transit for S3.
- RDS: require TLS, update JDBC or psql clients, and pin CA bundles.
- EKS or ECS: terminate TLS at the sidecar or app, consider mTLS if you need workload identity.
- PrivateLink: keep access inside AWS networks while still using TLS.
Once flows look clean in monitor mode for a solid window, say two weeks, move to enforce.
If you’re worried about client breakage, roll out redirects first at ALB. Then tighten server-side to TLS-only. For databases, turn on require SSL or TLS in nonprod, fix client configs, then promote to prod. For caches, enable in-transit encryption and rotate clients accordingly.
Forget the edges
Transit Gateway enable it
If two VPCs talk via Transit Gateway and only the VPCs are in enforce, you still need encryption controls on the TGW. Do it via Console or API using modify-transit-gateway. AWS says enabling on an existing TGW won’t cut traffic.
After enabling, with both TGW and all attached VPCs in enforce and no exclusions, you get encryption end to end for inter-VPC traffic.
Double-check attachments and routes. It’s common to fix one side and forget the other. Keep a simple table: VPC name, TGW attachment ID, control status, and last reviewed date. That turns tribal knowledge into a shared checklist.
Rollout without chaos
- Sequence: dev to staging to low-risk prod to high-throughput prod.
- Communication: publish a short aws encryption in transit standard and the enforcement calendar.
- Observability: build a dashboard around encryption-status trends; alert on plaintext sightings.
- Upgrades: plan instance family moves if you’re on older generations without hardware support.
- Tags: tag VPC encryption controls by owner and system; it’s your breadcrumb trail during incidents.
When in doubt, treat enforce like a firewall rule change. Use a change window, a rollback plan, and a crisp runbook.
People and process make or break this. Nominate a small encryption champions crew from platform, networking, and app teams. Give them shared dashboards and a weekly 15-minute stand-up until all prod VPCs are green. Momentum beats perfection.
Quick pit stop
- Start in monitor mode; baseline with encryption-status in flow logs.
- Fix ALB, S3, RDS, EKS or ECS, and TGW gaps first; those remove most hotspots.
- Run clean for 1–2 weeks; then flip enforce in waves.
- Enable enforcement on Transit Gateway for end-to-end inter-VPC protection.
- Keep exceptions rare, documented, time-bound, and tagged.
Add two more habits and you’ll stay ahead:
- Budget for logs: VPC Flow Logs volume grows with traffic. Pick S3 when you need longer retention and use Athena for queries to keep costs predictable.
- Bake it into templates: make enforce on the default in your VPC IaC module and landing zone, so new environments start compliant.
FAQ
Does this replace TLS
No. Nitro encryption protects links within AWS infrastructure. Application-layer TLS like HTTPS, database TLS, or mTLS protects end to end and provides identity. Best practice is both. The encryption-status signal helps you verify coverage across layers.
Enable enforce mode on VPCs
Not recommended. For existing VPCs, start in monitor mode. Use the findings to fix plaintext. After you’ve verified encryption everywhere, switch to enforce. For new VPCs, you can start with enforce at creation.
Cover traffic between VPCs
If you connect VPCs with Transit Gateway, you must enable encryption controls on the TGW too. With TGW and all attached VPCs in enforce and no exclusions, traffic is encrypted end to end across VPC boundaries.
Older EC2 instance types
Older generations may lack hardware encryption in transit. You should upgrade to supported instance types to fully benefit. Either way, keep application TLS in place for end-to-end protection.
Prove compliance to auditors
Export VPC Flow Logs with the encryption-status field as evidence. Bundle remediation tickets and include change records showing the move from monitor to enforce. Map the control to HIPAA, PCI DSS, FedRAMP, and NYDFS. Logs plus written policy usually satisfy control families for aws encryption in transit.
Enabling encryption on Transit Gateway
AWS indicates enabling encryption controls on an existing TGW does not interrupt flows. Still, treat it like a sensitive change. Schedule a window, monitor closely, and validate paths.
Look for plaintext flows fast
Send VPC Flow Logs to a place you can search at scale, like CloudWatch Logs or S3 with Athena. Create a simple query for encryption-status equals none, group by source and destination, and sort by bytes. That points you to the loudest offenders first.
Need PrivateLink or VPC peering
Yes. Private networking reduces exposure and data egress. Encryption in transit reduces risk if someone taps a link or misconfigures a path. Together, they’re stronger. Keep both, and keep TLS on top.
Path to enforced encryption
- Enable VPC Encryption Controls in monitor mode on one nonprod VPC.
- Turn on VPC Flow Logs and route them to a searchable destination.
- Build a query or dashboard for encryption-status and hunt plaintext flows.
- Fix low-hanging fruit: ALB HTTPS-only, RDS with TLS required, S3 aws:SecureTransport.
- Patch service-to-service calls to HTTPS or mTLS in ECS or EKS.
- Upgrade any unsupported instance families where needed.
- Enable encryption controls on Transit Gateway if you use TGW.
- Run clean for 1–2 weeks under peak load; document evidence.
- Move that VPC to enforce; monitor; repeat across environments.
- Lock in a standard: all new VPCs launch with enforce mode on day one.
A few extras to smooth the ride:
- Keep a known gaps list with owners and dates. If something needs time, like a third-party agent that’s HTTP-only, track it and review weekly.
- Rotate certificates on a schedule. Use ACM to issue and auto-renew where possible, so you don’t swap plaintext risk for expired cert outages.
- Add a lightweight SLO: 99.9% of flows must show encrypted status. That gives teams a number to watch and improve.
You want this to end with one outcome: zero plaintext. VPC Encryption Controls give you a safe, observable path to get there. Start in monitor, fix what’s noisy, then make encryption non-optional. The compounding benefit is huge: cleaner audits, lower breach risk, and a cloud posture that grows with you.
If you already enforce TLS at the app and S3 bucket level, this is your missing layer. Continuous, VPC-wide pressure that turns data encryption in transit best practices into defaults, not chores. Make encryption boring and automated, and your team can actually build.
References
- Amazon VPC Flow Logs documentation
- AWS Nitro System overview
- AWS Transit Gateway documentation
- AWS CLI modify-transit-gateway
- Application Load Balancer docs
- AWS Fargate overview
- Amazon S3: Require HTTPS (aws:SecureTransport) example policy
- Amazon S3 transport layer security
- AWS HIPAA compliance
- AWS PCI DSS compliance
- AWS FedRAMP compliance
- NYDFS Cybersecurity Regulation (23 NYCRR 500)
- Amazon RDS: Using SSL/TLS to encrypt a connection
- Amazon ElastiCache in-transit encryption
- AWS Certificate Manager (ACM) overview
- AWS PrivateLink overview
- CloudWatch Logs Insights
- Query Amazon VPC Flow Logs with Athena
- Tagging AWS resources
- AWS Well-Architected Framework, Security Pillar
- NIST SP 800-52r2 (TLS guidance)

