
Ditch API Keys with AWS Outbound Identity Federation
You shouldn’t be babysitting API keys in 2025. Keys leak, often. Keys get copied. Keys land in logs, laptops, and repos you forgot existed. The blast radius gets ugly, and cleanup is slow and super tedious.
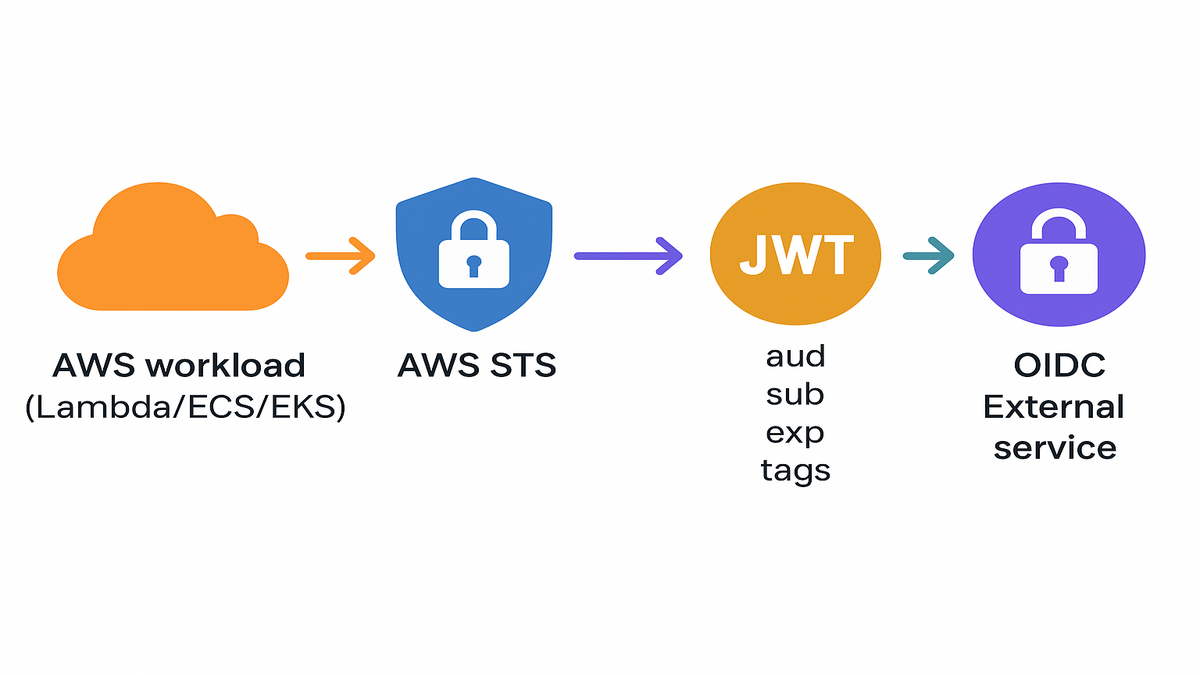
Here’s the flip: your AWS workloads can authenticate to external services with short-lived JWTs from AWS STS. No long-term credentials, seriously. No secret sprawl clogging everything up. Just standard OIDC, clear trust boundaries, and CloudTrail receipts for proof.
If you’ve ever Googled “aws iam outbound identity federation access login,” you know the docs rabbit hole. This is the practical, no-BS guide that skips fluff and weird detours. You’ll set it up once, enforce access with IAM policies, and pass tags as claims. After that, you’ll never store a static token again. Kinda freeing honestly.
Think of it like this: your compute proves “I am who I say I am,” and gets a token. That token lives only 5–15 minutes, then dies on its own. Your app calls the SaaS or multi-cloud API, job finishes, and the token disappears. Nothing to rotate, nothing to forget, nothing to stash under a rug.
TLDR
- Mint short-lived JWTs from AWS STS to call external services using standard OIDC.
- Ditch stored API keys; services trust your issuer URL and JWKS, not secrets.
- Use IAM to control who requests tokens and exactly which claims they receive.
- CloudTrail logs every issuance event; pass tags as claims to power ABAC.
- Best for multi-cloud access, SaaS calls from Lambda or ECS, and internal apps.
If API key sprawl burned you, or rotations keep wrecking your calendar, this scales. You bring tight IAM guardrails; the external service brings OIDC validation goodness. Everyone gets less risk, fewer support tickets, and a calmer on-call life.
What outbound federation means
Plain English STS JWTs
Outbound identity federation lets AWS workloads authenticate to external services using short-lived JWTs. You enable it with the IAM API action EnableOutboundWebIdentityFederation for your account. That action gives your AWS account a unique OIDC issuer URL to use. External services trust that issuer, pull your JWKS, and verify token signatures carefully.
In practice, your Lambda or ECS or EKS task calls AWS STS for a signed JWT. Then it presents that token to the external API like logging, CI/CD, or analytics. The token expires quickly, so you’re not hoarding any long-term secret anywhere. It’s simple once you walk through it once or twice.
Here’s the mental model: your workload already has an identity via an IAM role. Outbound federation lets that identity speak OIDC to services outside AWS directly. No side-channel keys, and no custom auth shims bolted on later. Just standards your partners and SaaS vendors already understand well.
Nice bonus here: on-demand, fast-dying tokens reduce credential reuse risk significantly. If an attacker snapshots a container, they won’t find anything durable anyway. Maybe they grab a short-lived token with a tight audience. By the time they try to use it, it probably already expired.
Why this beats secrets
- Eliminate secret sprawl by stopping API keys in env vars or source control.
- Tight control through IAM policies for audience, lifetimes, and who can request tokens.
- Auditability with CloudTrail recording token issuance events for each request.
- ABAC power by passing resource tags as custom claims used for authorization.
First-hand example: a Lambda posts build statuses to a SaaS every single deploy. Instead of stuffing API keys in Parameter Store, the function mints a JWT. It’s limited to aud=build-status and exp=10m, clear and tight controls. Breach the box and there’s nothing durable to steal from it.
If rotating an API key in six places once paused your deploy, this feels magical. You centralize control in IAM and enforce strict, narrow audiences everywhere. Short expirations handle cleanup, so nothing lingers beyond its window. The workload never holds a secret; it borrows one briefly, then loses it.

OIDC trust and tokens
Issuer URL and JWKS
When you call EnableOutboundWebIdentityFederation, IAM returns your account’s issuer URL. You configure that URL in the external service as an OIDC identity provider. The service fetches your JWKS endpoint to validate signatures on each token. From there, standard OIDC rules apply for signature, audience, expiry, and subject.
This is straight RFC territory, not some risky garden path approach. JWT and JWK specs define the token format and key distribution cleanly. Or as RFC 7519 says, JWT is a compact, URL-safe claim format. It’s boring and predictable in a very good way, thankfully.
You don’t need to overthink discovery either, really don’t. Most OIDC-capable services auto-discover issuer metadata via well-known endpoints. They fetch the JWKS on a regular interval to keep keys fresh. If they validate issuer, audience, expiration, and signature, tokens work great.
Token claims and tags
You control token shape with IAM policies, with precise limits. Policies can restrict the audience claim to specific external apps or tenants. Policies can bind the subject claim to the calling workload’s identity. They can cap the expiration to tight 5–15 minute windows easily. They can pass custom claims using tags for ABAC, like project=alpha.
A realistic path: 1) External service trusts your issuer URL and enforces aud="analytics-ingest" strictly. 2) Your ECS task role requests tokens only for that specific audience value. 3) Tags on the task inject claims like team=DataOps for clear ownership. 4) The external service authorizes by claims, not per-user keys to manage.
Think of tags as your simple, shared policy vocabulary for everyone. Keep names simple and consistent like env, team, costcenter, and dataclass. Document them clearly so no one guesses weird tag names. When every workload uses the same tags, policies stay clean across environments.
Pro tip: start with conservative default expirations like five to ten minutes. Grant longer tokens only when latency or batch size truly demands it. Tight windows limit replay risk and reduce lateral movement opportunities. You’ll sleep better with stricter lifetimes baked straight into policies.
Real use cases
Multicloud workloads no secrets
If you orchestrate across AWS and another cloud, you can ditch keys. Your AWS workload mints a JWT and presents it to a gateway elsewhere. That gateway validates via your issuer URL and verifies the signature carefully. No cross-cloud secrets vaulting and no ugly key rotation calendars.
Concrete scenario: an EKS job kicks off a pipeline in another cloud. The external gateway accepts tokens with aud=pipeline-trigger and exp<900s only. If someone replays the token later, it’s completely useless garbage. That tight expiry window makes a big difference in practice.
You can also slice access by tenant using claims carried inside tokens. A shared pipeline service can recognize claims like tenant=eu-west or specific region. It routes jobs correctly and enforces data residency without extra keys. No separate keys per tenant and no manual rotation messes.
SaaS integrations Lambda containers
Most modern SaaS platforms support OIDC or custom JWT validation now. Your Lambda calls an analytics API, monitoring platform, or CI service directly. It presents a short-lived JWT, not a secret copied across repos anymore. Claims carry context like team and environment for authorization decisions.
First-hand example: a containerized workload pushes logs to an observability vendor. You enforce aud and exp in IAM with clear, tight boundaries. You set tags for cost_center and env that become claims automatically. The vendor maps claims to routing, retention, or access tiers easily.
Another win here is much simpler offboarding across your environments. If you sunset a workload or service, change the role permissions immediately. Detach or delete the role’s token-minting permissions to disable access. No hunting stale keys in CI, IaC templates, or old runbooks ever.
Internal apps without logins
Got internal APIs, gateways, or service mesh sidecars quietly running? Configure them to trust your AWS issuer URL as an OIDC identity provider. Now workloads authenticate with the same OIDC foundation across everything. No separate username, password, or API key lifecycle to babysit.
This pairs nicely with mTLS inside the mesh for transport security purposes. mTLS proves you have a trusted, encrypted channel between services. OIDC proves the caller is allowed to do X for Y minutes. Together you get strong identity and short, enforceable lifetimes.
Security governance gotchas
Least privilege and IAM conditions
Lock it down like you really mean it, not halfway. Use IAM policies to allow only specific roles to request tokens safely. Restrict audiences to a known set like payments-api or ci-trigger only. Limit token lifetimes to minutes, not hours, even if someone complains. Pass only the tags you truly need as custom claims to external services.
ABAC tip: tags like env, project, and data_sensitivity can travel as claims. Keep the vocabulary tight, short, and well audited over time.
Extend guardrails with conditions for extra safety in production. Allow minting only from certain VPCs or subnets that you fully trust. Or allow during certain hours for batch jobs, not around the clock. Even if a role is compromised, these restrict what an attacker does.
CloudTrail and drift detection
CloudTrail logs token issuance so you can answer who minted what and when. Also for which audience and which role requested it, with real receipts. Alert on unusual token churn like spikes outside business hours in prod. Periodically confirm external services use the correct issuer and JWKS.
First-hand example: a team widened allowed audiences during a fire drill. They forgot to revert later, which happens in stressful incidents sometimes. A weekly policy diff caught the drift and prevented bigger problems. External services had stricter aud checks, so it didn’t blow up.
Operational hygiene you’ll want, trust me:
- Monitor failure codes from external services like invalid audience or expired token.
- Spikes often mean config drift, clock skew, or a forgotten rollout somewhere.
- Watch for token minting from unexpected roles, regions, or weird hours.
- Alerts should be actionable: who, what audience, and which environment exactly.
Identity Center SAML limits
Quick compare time: IAM Identity Center is for people signing into consoles. That’s workforce access using SAML or OIDC for humans doing human tasks. Outbound identity federation is for workloads, not human users at all. Your Lambda or ECS authenticates to external services via short-lived JWTs.
If automating setup across accounts, you might hit service throttles sometimes. You’ll see errors like enable iam identity center rate exceeded on provision. Use exponential backoff with jitter and respect service quotas carefully. If your SaaS offers AWS SSO for workforce SSO, use it separately.
Also consider clock skew because JWT validation is time sensitive. Keep NTP healthy in your environments and on any edge compute nodes. Otherwise you’ll chase phantom expired token errors caused by bad clocks. It’s annoying and wastes time, so fix clocks early.
Implement tokens in stack
Enable feature set guardrails
- Call EnableOutboundWebIdentityFederation and record your unique issuer URL safely.
- Create IAM policies allowing specific roles to request tokens with limits enforced.
- Control audience, lifetime, and which tags can appear as token claims.
- Attach policies to the exact roles used by Lambda, ECS, or EKS workloads.
First-hand example: only your prod ECS task role mints aud="payments-api" tokens. It must use exp≤600s and include env=prod and service=billing claims. That keeps the surface tight and clean while staying flexible enough.
Add a preflight checklist so you don’t miss basics:
- Confirm which external services will trust your issuer, environment by environment.
- Define your tag vocabulary and ownership between platform and app teams.
- Decide default max expiry like ten minutes, with exceptions documented.
- Document audiences like payments-api, ci-trigger, and analytics-ingest with owners.
Configure external service trust
- In the external service, add your issuer URL as an OIDC identity provider.
- Import the JWKS or point to its URI to verify signatures constantly.
- Enforce aud, exp, and issuer match; map claims to permissions or tenants.
If the service supports ABAC, map tags like team or project to roles. Keep claim names stable and documented so partners don’t guess anything.
External-side guardrails that really pay off in practice:
- Cache JWKS briefly and refresh on key ID misses automatically.
- Require HTTPS and validate TLS correctly when fetching discovery or JWKS.
- Treat unknown claims as non-authoritative; trust only the expected ones.
Mint tokens from code
- In Lambda, call AWS STS to request a web identity token for your audience.
- In ECS or EKS, use the role to request a token and call the API.
- Send Authorization: Bearer
and handle refresh within the lifetime. - Never persist tokens to disk; keep them in memory and short-lived.
Operational tip: log token issuance metadata, not the token value itself. If a call fails, check audience mismatch or expired token first. Also confirm the issuer configuration on the external side matches yours. Those three cause most bugs, honestly, more than anything else.
Workflow pattern that scales across teams reliably:
- Build a tiny in-process token client library for requests and caching.
- Cache tokens briefly, retry with jitter, and expose basic metrics cleanly.
- Add non-prod debug endpoints: validate token locally and force refresh.
- Keep audience and claim tags in config, not code, to avoid redeploys.
Testing and rollout
- Start in a dev account with one audience and a single service first.
- Write negative tests for wrong audience, expired token, or missing tag.
- Test rotated key IDs to verify JWKS refresh works under pressure.
- Add canary workloads that call every few minutes and alert on failures.
- Roll out to stage, then prod, by audience with clear change control.
- Keep a rollback switch to disable token minting if something breaks.
Migration plan from API keys that won’t wreck prod:
- Run dual auth for a week behind a feature flag, keys and tokens.
- Compare error rates and latency; fix clocks and audience typos quickly.
- Turn off key-based auth per endpoint once tokens stay stable reliably.
- Delete keys from secret stores and remove their usage in CI configs.
Your 60 second pulse check
- You enabled outbound federation and received a unique issuer URL already.
- External services trust your issuer and fetch your JWKS successfully.
- IAM policies gate who mints tokens, with tight audience and expiry controls.
- Tags flow as custom claims for ABAC enforcement on the external side.
- Workloads call SaaS or multi-cloud APIs using short-lived JWTs, not stored keys.
If you can check all five, you’re running Zero Trust for service calls. It’s short-lived, verifiable identity at runtime, not stored in files. No long-term secrets to babysit or leak during some long night.
FAQ fast answers
- Q: How is this different from AWS IAM Identity Center and SAML?
A: Identity Center is workforce access for people, via SAML or OIDC. Outbound federation is workload access using short-lived JWTs from AWS STS. Your Lambda or ECS talks to external services without long-term secrets, ever.
- Q: What’s the token lifetime and how do I choose it?
A: Keep it short, minutes not hours, with IAM policy caps. Use 5–15 minutes based on needs, and avoid longer without reason. Short lifetimes limit replay and shrink the blast radius meaningfully.
- Q: How do external services validate the token?
A: They use your issuer URL and fetch JWKS to verify signatures carefully. They enforce audience, subject, and expiry checks with strict verification. Many platforms support OIDC natively; otherwise use standard validation libraries.
- Q: Can I pass tags as claims for authorization?
A: Yes, IAM can propagate selected tags as custom claims very easily. External services can apply ABAC policies like team=Payments or env=prod. No separate workload identity directory needed for that policy mapping.
- Q: What if I rotate signing keys or the JWKS changes?
A: OIDC clients should cache JWKS and refresh it periodically on schedule. Most libraries handle rotation if issuer and key IDs stay consistent. Test rotation in non-prod and confirm refresh cadences match reality.
- Q: We’re hitting API throttles (“rate exceeded”) during setup—now what?
A: Use exponential backoff with jitter, and sequence your provisioning. If enabling Identity Center and federation broadly, stagger your rollout. Respect service quotas to avoid noisy failures and flaky pipelines.
- Q: What about latency—does minting a token slow us down?
A: Minting is fast and easily cached in-process for a short window. Request just before the call and reuse briefly, then refresh on demand. This keeps overhead low while keeping expirations short and safe.
- Q: How does this help with compliance?
A: Auditors want least privilege, short-lived creds, and traceability today. IAM defines who can mint what, and tokens expire quickly by default. CloudTrail logs issuance, so you can show who did what and when.
- Q: Any pitfalls with multi-account setups?
A: Standardize tag names and audiences across accounts, then manage centrally. Use AWS Organizations guardrails to limit who can mint for specific audiences. That keeps policy drift low and reduces surprises during audits.
Launch playbook
- Enable outbound web identity federation and capture issuer URL and JWKS URI.
- Define IAM policies for minting, audiences, max expiry, and allowed claim tags.
- Configure OIDC trust in external services and enforce issuer, aud, and exp.
- Update workloads to request tokens just-in-time; add retry and backoff logic.
- Log issuance metadata and alert on anomalies surfaced through CloudTrail.
- Run chaos tests for expired token, wrong audience, rotated keys, and missing claims.
Wrap this up in a week and sunset half those rotation calendar invites. The big idea: move identity proof to runtime, not some secrets store. Tokens mint per call, get inspected per call, and die fast afterward. That’s tighter security, cleaner ops, and fewer 2 a.m. key leak incidents. Next step: pick one integration and just ship it this sprint. After the first win, standardize, templatize policies, and retire dusty secrets.
References
- RFC 7519: JSON Web Token (JWT)
- RFC 7517: JSON Web Key (JWK)
- RFC 6750: The OAuth 2.0 Authorization Framework: Bearer Token Usage
- RFC 7523: JSON Web Token (JWT) Profile for OAuth 2.0 Client Authentication and Authorization Grants
- OpenID Connect Core 1.0
- OpenID Connect Discovery 1.0
- AWS Security Token Service (STS) API Reference
- AWS IAM: Attribute-Based Access Control (ABAC)
- AWS CloudTrail User Guide
- AWS Organizations
- OWASP JSON Web Token (JWT) Cheat Sheet
- NIST SP 800-207: Zero Trust Architecture

