
Scale S3 Access Fast With Tag Based ABAC
You’re probably still hand-wiring S3 perms like it’s 2017. Static IAM policies, bucket ARNs copy‑pasted into JSON, and endless policy sprawl. Attribute-based access control (ABAC) for Amazon S3 general purpose buckets fixes that. It matches tags on IAM principals to tags on buckets and Access Points.
If that sounded like magic, here’s the simple version. Add the same meaningful tags to your S3 resources and to the IAM roles that need them. When the tags match, permissions click into place automatically. No more chasing bucket names or trying to remember who should see what. You shift from “grant access to bucket X” to “grant access to anything tagged project=alpha, environment=prod.”
This is how large teams avoid permission chaos. It scales with your org as you add teams, projects, and buckets without rewriting policies every week. It’s also easier to audit. You can literally ask, “Who can touch restricted data?” Then answer it by checking tags and a couple policies, not 47 scattered JSON files.
TL;DR
- Tag S3 buckets/Access Points and IAM principals; access is granted when tags match.
- Use aws:ResourceTag and aws:PrincipalTag for least-privilege comparisons.
- Standardize tags (project, team, environment, dataclassification, costcenter).
- No extra cost; available in all Regions; works via console, CLI, SDKs, CloudFormation.
- Prevent tag drift with guardrails (SCPs, IaC checks, automation).
Let’s break down what changed, how to design tags that won’t bite you later, and the exact policy snippets that make this feel like autopilot instead of whack‑a‑mole.
What changed
- ABAC now works directly for S3 general purpose buckets; Access Points support tags too.
- Policies scale with your org: add a bucket, tag it, and roles with matching tags get access automatically.
That second bullet is the unlock. Before, you hardcoded resource ARNs. Every new bucket meant another policy edit. With ABAC, you describe intent once. If a role’s tags match a bucket’s tags, allow list/read/write. It’s like group membership, but the “groups” are attributes you control (project, environment, data_classification).
Also crucial: Access Points support tags and are great for scoping access to shared datasets. You can tag the Access Point and enforce per‑team or per‑environment rules without copying data or making bucket sprawl.
Why ABAC for S3 now
- It reduces policy sprawl. One parametric policy replaces dozens of resource‑specific ones.
- It matches how teams organize work: projects, teams, environments, classifications.
- It’s self‑service. New projects get access by tagging their roles, not by asking security to edit JSON.
- It’s auditable. You can answer “who can access what” by reviewing tag rules and conditions.
ABAC isn’t just “easier.” It’s safer when done right because least privilege hangs off your tags. Instead of hoping someone removed an old bucket ARN from a policy, access naturally drops when tags stop matching.
Design your tags
- Prefer stable attributes: project, team, environment, dataclassification, costcenter.
- Enforce naming conventions and required tags via IaC, CI, and SCPs.
A few practical notes
- Keep tags stable across time. ‘project’ beats ‘sprint’ or ‘release’. ‘environment’ beats ‘branch’.
- Keep values short, lowercase, and consistent. ‘prod’ not ‘Production’. ‘team_data’ not ‘Team Data’.
- Use a small, fixed set for critical attributes. example: environment in [dev, test, stage, prod].
- Don’t put secrets or PII in tags. Tags are metadata, not a secret store.
- Plan for limits. Many AWS resources support up to 50 tags per resource (plenty for ABAC).
- Consider AWS Organizations tag policies to standardize keys/values across accounts.
Helpful tagging commands
- Tag a bucket: aws s3api put-bucket-tagging --bucket my-bucket --tagging 'TagSet=[{Key=project,Value=alpha},{Key=environment,Value=prod}]'
- Get bucket tags: aws s3api get-bucket-tagging --bucket my-bucket
- Tag an IAM role: aws iam tag-role --role-name DataEngineerAlpha --tags Key=project,Value=alpha Key=environment,Value=prod
Policy building blocks
- aws:PrincipalTag/
: tag on the caller (user/role). - aws:ResourceTag/
: tag on the S3 bucket or Access Point.
Conditions check these at evaluation time. If they match, you’re in. If not, you’re out. Combine these with actions (like s3:ListBucket and s3:GetObject). Then scope your Resource to bucket ARNs and object ARNs properly.
Two reminders
- Listing a bucket needs a policy on the bucket ARN (arn:aws:s3:::bucket-name). Getting/putting an object needs arn:aws:s3:::bucket-name/*.
- Explicit Deny beats Allow. Use this to gate sensitive data.
Example allow list/read/write
{ 'Version': '2012-10-17', 'Statement': [ { 'Sid': 'ListOwnProjectBuckets', 'Effect': 'Allow', 'Action': ['s3:ListBucket'], 'Resource': 'arn:aws:s3:::', 'Condition': { 'StringEquals': { 'aws:ResourceTag/project': '${aws:PrincipalTag/project}' } } }, { 'Sid': 'ReadWriteObjectsForProject', 'Effect': 'Allow', 'Action': ['s3:GetObject', 's3:PutObject'], 'Resource': 'arn:aws:s3:::/*', 'Condition': { 'StringEquals': { 'aws:ResourceTag/project': '${aws:PrincipalTag/project}' } } } ] }
What’s happening
- Both statements use a wildcard Resource with a tag condition. Only tagged buckets/objects with project equal to the caller’s project match.
- List and object actions are separated because S3 evaluates them on different resources (bucket vs bucket/*).
- You don’t need to enumerate every bucket ARN; tags do the filtering.
Want to allow multiple projects per role? Use multi‑valued tags (e.g., project=alpha,beta). Then use the ForAnyValue:StringEquals operator in your Condition.
Harden with environment and classification
- Add environment matching: require aws:ResourceTag/environment == ${aws:PrincipalTag/environment}.
- Use explicit Deny for sensitive data: if aws:ResourceTag/data_classification == restricted, deny unless aws:PrincipalTag/clearance == restricted.
- For object rigor, pair with s3:ExistingObjectTag and s3:RequestObjectTag to ensure object tags are present and correct.
Simple Deny block
{ 'Sid': 'DenyRestrictedWithoutClearance', 'Effect': 'Deny', 'Action': 's3:', 'Resource': ['arn:aws:s3:::', 'arn:aws:s3:::/'], 'Condition': { 'StringEquals': {'aws:ResourceTag/data_classification': 'restricted'}, 'ForAllValues:StringNotEquals': {'aws:PrincipalTag/clearance': 'restricted'} } }
For uploads enforce object tags
- Require writers to include an object tag like data_classification on PutObject using s3:RequestObjectTag conditions.
- Require that existing objects retain correct tags on overwrite using s3:ExistingObjectTag.
This makes your data lake self‑describing. Downstream tools can filter by tags without parsing paths.
Gotchas and guardrails
- Tag drift breaks ABAC: enforce required tags at creation (IaC), block untagged resources in CI, and audit regularly.
- Scope Resources precisely (bucket and bucket/*) and favor least privilege.
- Remember: explicit Deny beats Allow.
Extra safety rails
- Use AWS Organizations SCPs to prevent untagged creation in critical accounts. Example: block s3:CreateBucket unless performed by approved pipelines.
- Use AWS Config’s required-tags managed rule to detect and alert on missing tags.
- Use IAM Access Analyzer policy validation to catch overly broad conditions.
- Treat break‑glass roles carefully. Keep a monitored, time‑limited, highly privileged role for emergencies and exclude it from ABAC where needed.
- Understand tag update timing. Tag changes are generally immediate, but caches may delay effects; test before high‑stakes changes.
- Watch the tag limit. Design your ABAC around a handful of keys, not dozens.
- For cross‑account, ensure both sides use consistent tag keys. Make sure resource‑based policies don’t override your intent.
ABAC on S3 model
- Principal attempts action (list, get, put) on a bucket/object.
- IAM evaluates identity‑based policy conditions with aws:PrincipalTag.
- S3 evaluates resource‑based policy or Access Point policy conditions with aws:ResourceTag.
- If at least one Allow matches and no Deny matches, request is allowed.
This is why “matching tags” language is handy. You aren’t granting blanket access. You’re stating a rule that only passes when attributes align.
Operationalizing tags at scale
- Infrastructure as Code: bake required tags into CloudFormation, CDK, or Terraform modules. Fail PRs that omit them.
- CI checks: run policy‑as‑code and tag linters in pull requests.
- Event‑driven fixers: detect untagged buckets with Config or EventBridge and auto‑tag or quarantine.
- Tag editor: use AWS Resource Groups Tagging API or the console Tag Editor to remediate gaps fast.
- Consistent dictionaries: define an org‑wide tag policy for keys and allowed values.
CloudFormation pattern
Quick CloudFormation pattern (conceptual): ensure every S3 bucket resource includes Tags with project, environment, and data_classification. Then wire a custom rule to block stacks missing these.
Access Points friend of ABAC
S3 Access Points let you expose a controlled entry door to shared buckets. You can:
- Tag the Access Point with project or environment and use aws:ResourceTag on the Access Point.
- Attach a policy to the Access Point that enforces tag conditions, separate from the bucket policy.
- Give each team its own Access Point with per‑team network and permission boundaries.
This reduces blast radius while keeping one authoritative copy of the data.
Session tags temporary power up
You can pass session tags when assuming roles to make ABAC more flexible:
- Use sts:TagSession to add attributes like project or clearance at session time.
- Control who can set which session tags using IAM conditions on sts:TagSession and aws:TagKeys.
This is gold for contractors or ephemeral CI jobs. No need to create permanent roles for every project. Assume once with the right tags, and your ABAC policy does the rest.
Testing and debugging
- IAM Policy Simulator: sanity‑check your Allow/Deny logic with tag conditions.
- CloudTrail: verify that evaluation matched your expected tags and see AccessDenied vs Allowed.
- Access Analyzer: validate policies and surface findings for public or cross‑account exposure.
- S3 server access logs or CloudTrail Lake: look for unexpected denies and tune conditions.
If something fails
- Confirm both sides are tagged exactly, including case.
- Verify you used StringEquals vs StringLike appropriately.
- Ensure you scoped resources (bucket and bucket/*) correctly.
- Check for lurking explicit Deny in SCPs or resource policies.
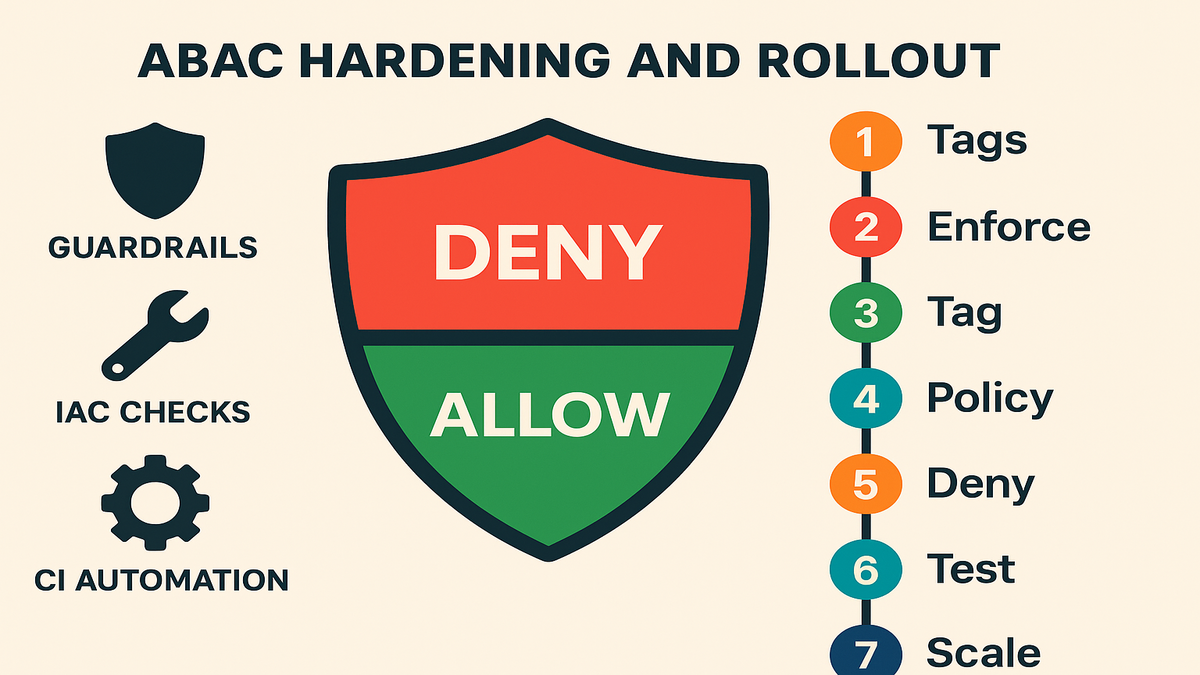
Rollout steps
(30 minutes)
1) Define canonical tags: project, team, environment, dataclassification, costcenter. 2) Enforce required tags in IaC and CI; add SCPs blocking untagged CreateBucket. 3) Tag pilot buckets/Access Points and IAM roles with matching attributes. 4) Apply ABAC policies using aws:ResourceTag and aws:PrincipalTag equality. 5) Add Deny for restricted data unless clearance matches. 6) Test list/read/write flows; validate in CloudTrail. 7) Expand to more teams; monitor and iterate.
In practice
- Step 1: publish a 1‑page tag spec. Lock down values for environment and data_classification.
- Step 2: update your Terraform/CloudFormation modules to require these tags. Add a CI check that fails if tags are missing or malformed.
- Step 3: pick two buckets, tag them, and tag one role for alpha‑dev and one for alpha‑prod. If you use Access Points, tag those too.
- Step 4: attach the sample ABAC policy to the roles. Keep your old policies as a backup but disable them for the pilot.
- Step 5: add the explicit Deny block for restricted data. Test access with and without the clearance tag.
- Step 6: run aws s3 ls and aws s3 cp tests from each role session. Check CloudTrail for Allowed/Denied events and confirm tag values in the event record.
- Step 7: write down what worked, fix gaps (naming consistency, missing tags), and roll out to the next team.
Real world scenarios
- Per‑project data lakes: one shared bucket, many prefixes. Teams use Access Points tagged with their project and environment. ABAC policies grant list/read/write only when tags match. No more prefix‑based inline allow‑lists.
- Multi‑environment isolation: developers can only access buckets tagged environment=dev or test. Production roles are locked to prod. Crossing the streams simply doesn’t match.
- Restricted datasets: buckets tagged data_classification=restricted are only visible to roles with clearance=restricted. Everyone else sees AccessDenied, even if they match on project.
- Temporary jobs: a CI role assumes a session with project=beta for a build. It uploads artifacts with required object tags, then loses access when the session ends.
Common questions
- Do I need to retag existing buckets?
Yes. ABAC won’t work without resource tags. Start with a pilot and script the rest.
- Will this cost me more?
There’s no extra charge for using tags or ABAC logic itself. Standard S3 and IAM pricing applies.
- Can I use this across accounts?
Yes. Align tag keys/values across accounts, and ensure resource policies and SCPs don’t collide with your ABAC logic.
- What about object ACLs?
Prefer bucket‑owner enforced Object Ownership and keep ACLs disabled; ABAC plays best with centralized policies.
- How many tags is too many?
Keep ABAC to a small core: project, environment, dataclassification, team, costcenter. Avoid building complex logic on dozens of tags.
- How do I stop tag drift?
IaC guardrails, CI checks, AWS Config rules, and periodic audits. Make tags part of your definition of done.
A quick checklist
- Chosen canonical tag keys and values.
- Buckets and Access Points tagged consistently.
- IAM roles tagged consistently (or session tags in place).
- Identity‑based ABAC policy attached and scoped to s3 actions needed.
- Explicit Deny for restricted data and a verified clearance process.
- Config and Access Analyzer watching your back.
- CloudTrail validation scripted for regression tests.
Switching S3 to ABAC is one of those upgrades that feels small and then changes your velocity. You tag once, you stop rewriting policies, and the right people get the right access by default. Cleaner reviews. Faster onboarding. Fewer 2 a.m. “can’t read the bucket” pings.
If your team has been drowning in permission snowflakes, this is the rope. Take 30 minutes, run the pilot, and let matching tags do the heavy lifting.
References
- IAM ABAC intro
- Access using tags
- S3 policy keys (including s3:ExistingObjectTag and s3:RequestObjectTag)
- S3 Access Points
- Tagging limits
- S3 pricing
- IAM policy evaluation logic
- AWS Organizations tag policies
- AWS Config required-tags managed rule
- IAM Access Analyzer policy validation
- AWS CloudTrail for S3 data events
- Session tags with STS
- S3 Object Ownership and ACLs

