
Amazon Kiro: Your AI Co-pilot for Cloud Workflows
You’re drowning in tickets, juggling pipelines, and guarding your weekend from incidents. Then AWS drops a new AI-powered service—Amazon Kiro—for complex cloud workflows and real-time decisions. If it delivers, your ops calendar just got lighter, big time.
Here’s the punchline: early notes say Kiro blends generative AI with AWS-native automation. Think intelligent routing, safe infrastructure changes, and assistants that understand your stack. Not a chatbot toy—it’s more like an ops brain, honestly.
If you’ve tried gluing Bedrock, Lambda, and Step Functions into a “smart” ops pipeline, you know the pain. Kiro looks like the out-of-the-box version—less YAML acrobatics, more shipping.
If your team lives on runbooks, on-call rotations, and scripts, Kiro could help standardize that tribal knowledge. Not magic, but fewer manual steps, safer changes, and quicker choices when graphs go red.
Let’s be real: the best ops is boring ops, period. If Kiro cuts noisy toil and speeds safe tasks—restarts, rollbacks, scaling, drift fixes—you win back hours. That’s not hype; that’s real breathing room for your team.
TLDR
- Amazon Kiro targets AI-driven cloud workflows and real-time assistance, on purpose.
- Expect managed, integrated automation, not a generic chat interface, please.
- Amazon Q vs Kiro: Q answers and creates; Kiro executes and orchestrates.
- No public amazon kiro launch date or downloads yet, for now.
- Mentions of an “Amazon Kiro IDE” are speculative—wait for official plugins.
- Start prepping now: define guardrails, pilot narrow workflows, and instrument results.
If you’ve waited for AI that actually does things, with receipts, watch this lane. Treat Kiro like an execution layer with approvals, not a magic wand. Teams that prep now will move faster when GA finally arrives.
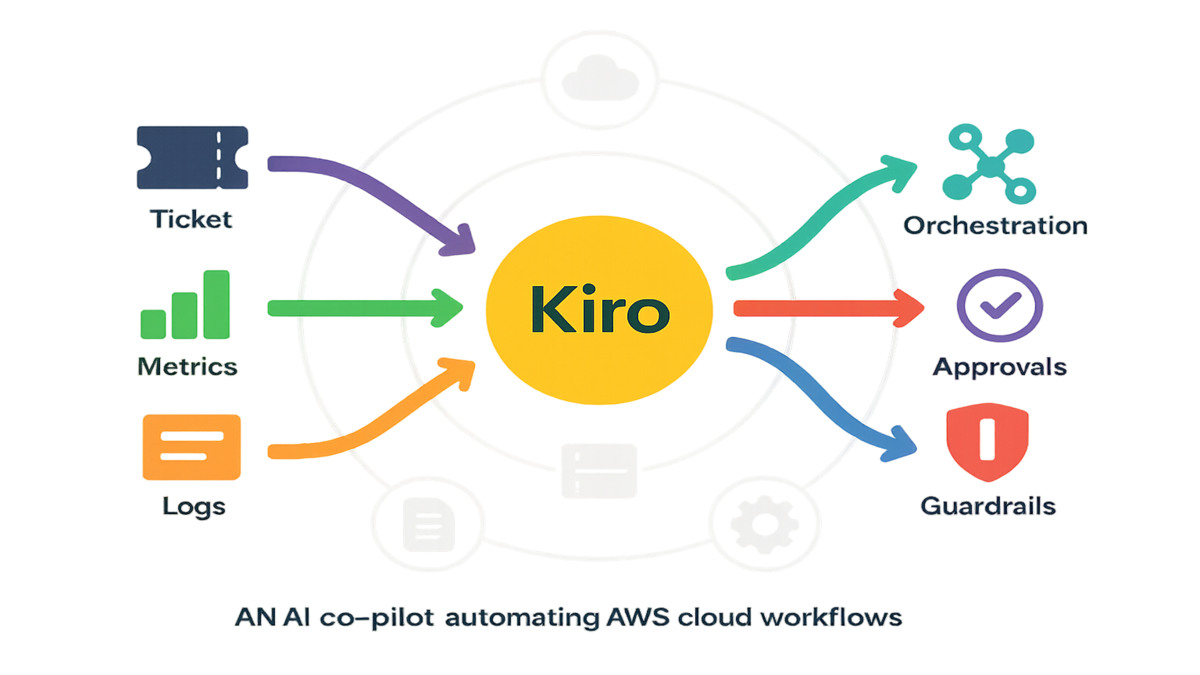
Meet Amazon Kiro
What we know now
From the launch roundup: Amazon Kiro is a new AWS service with built-in generative AI. It aims to enhance cloud workflows and automate complex tasks. It uses advanced models for smart decisions and real-time assistance, strengthening AWS’s AI push.
Translation for you: fewer manual runbooks, more automated, explainable actions. Instead of stitching prompts to pipelines yourself, you’d configure policies, connect services, and let Kiro propose or execute actions. Expect native hooks into logging, metrics, and approvals so changes don’t go rogue.
Think about the day-to-day: tickets arrive, alarms fire, someone scans logs, connects dots, then runs a runbook. Kiro’s pitch is to shorten that path. It detects the signal, suggests the fix, then runs it or waits for approval. The output is not just action, but traceable reasoning for your change control process.
Expect configuration over construction. Don’t write glue code for every event; define intents and boundaries instead. State what’s allowed, under which conditions, and who approves. The AI reads metrics and logs for context, then picks the next safe step.
How it plugs into AWS
Given AWS patterns, expect Kiro to sit beside a few usual suspects. Use Amazon Bedrock for model access, and AWS Step Functions for orchestration. You’ll also lean on AWS Systems Manager for operations. IAM gates what Kiro can do, and CloudTrail records its actions.
Think: “Scale this service by 30% if p95 latency > 400ms for 5 minutes, notify on-call, and open a ticket with context.” Kiro proposes, you approve, or auto-approve within limits, and everything’s auditable. That’s a huge upgrade over static rules and rigid playbooks.
Zooming in on likely plumbing:
- Event ingestion: CloudWatch Alarms or EventBridge route signals to Kiro. EventBridge patterns help filter noisy events and shape payloads.
- Decisioning: Bedrock-hosted models help classify incidents, find probable causes, and propose safe actions using your stated policies.
- Orchestration: Step Functions or Systems Manager Automation documents execute sequences: drain traffic, restart tasks, verify health, roll forward or back.
- Controls: IAM roles, resource-based policies, and possibly AWS Organizations guardrails keep actions scoped. AWS Config can enforce drift checks before any change.
- Audit: CloudTrail and service-specific logs capture who/what/when. Expect Kiro to leave rich breadcrumbs: inputs, plan, outcome.
A realistic example chain:
- EventBridge receives a “5xx spike” pattern from an ALB alert.
- Kiro correlates with CloudWatch metrics and error logs, fast, today.
- Proposed action: increase ECS service desired count by 2, warm cache, verify latency, and open a ticket if errors persist.
- Approval: auto-run in staging; in production, require on-call approval, only. CloudTrail records every step for audit and later review, anyway.
What Kiro is not
It’s probably not a one-click replacement for your current tooling. It won’t magically fix a broken architecture, sadly, for you. It’s also unlikely to be a local download; you don’t install most managed AWS services. If you’re searching for those downloads, think managed service plus optional IDE integration, not standalone.
It’s not a hall pass to skip change management, not at all. It thrives with strong process: named environments, least-privilege roles, clear approvals, and rollback plans. AI can accelerate bad habits, too, if you let it.
Watch out for anti-patterns:
- Turning on wide-open permissions “for testing,” then forgetting to lock them.
- Letting AI escalate privileges to force a change through, today.
- Skipping post-change verification and health checks, then hoping for the best.
- Blending prod and non-prod rules, which always bites later, hard.
Keep the boring guardrails, please, they are what save you. That’s how you move faster without chaos, every day, honestly.
Why Kiro bends ops
Speed without chaos
Generative AI already speeds up dev workflows across many teams. A GitHub study found developers finish tasks up to 55% faster with AI pair programming. Apply that speed to cloud ops—triage, fixes, and deploys—and you compress MTTR with humans in the loop.
Kiro’s edge is being AWS-native, with less glue and better context. Fewer scripts, richer context from metrics, logs, and topology, and consistent permissions. You get assisted decisions based on reality, not guesses anymore.
Speed isn’t recklessness; it’s cutting down wait states, a lot. Handoffs between detection, diagnosis, approval, and execution turn minutes into hours. An AI orchestrator can slash those waits, especially for known failures and common mitigations.
Governance by design
AI that acts needs strict guardrails to stay safe, always. Expect Kiro to honor IAM roles, scoped permissions, and change approvals. Picture rules like this. Kiro can restart ECS tasks in staging automatically, but production requires PagerDuty approval and a matching CloudWatch pattern.
Auditing is non-negotiable, seriously. With CloudTrail events and change logs, you can answer what, why, and who approved. That’s essential for regulated environments and audits.
Add extra layers:
- AWS Systems Manager Change Manager for formal change requests and windows.
- AWS Config rules to block actions when resources are out of compliance.
- Service Control Policies (SCPs) to prevent cross-account surprises from happening.
- Well-Architected reliability checks to validate blast radius assumptions before changes.
Upside for your roadmap
McKinsey estimates generative AI could add $2.6T–$4.4T each year across the economy. In your world, the unlock is time: move from firefighting to proactive engineering. If Kiro clears even 20–30% of repetitive ops work—scaling, restarts, and routine config fixes—you reclaim sprints.
The play isn’t novelty; it’s boring reliability at scale, instead. AI quietly keeps your platform green while your team builds the next capability.
A simple ROI frame:
- Baseline toil (hours/week): paging, manual restarts, drift fixes, reports, per team.
- Target automation: pick 3–4 tasks, estimate frequency times duration for each.
- Savings: reclaimed hours x fully loaded cost, per quarter.
- Quality bonus: fewer handoffs, fewer incidents per deploy, faster reviews.
That’s how you justify a pilot without a dramatic pitch deck.
Pulse check
- Kiro is positioned as AI-driven workflow automation for AWS— not a chatbot.
- Expect orchestration and real-time assistance with native permissions and audits built-in.
- It likely leans on Bedrock, Step Functions, and Systems Manager together.
- Speed is the win, but governance is the moat that protects.
- No confirmed amazon kiro launch date or downloads as of today.
If that sounds like your ideal weekend, you’re not alone at all. Treat Kiro as an automation co-worker with perfect memory and strict boundaries. Train it on routine work; let humans handle ambiguity and design choices.
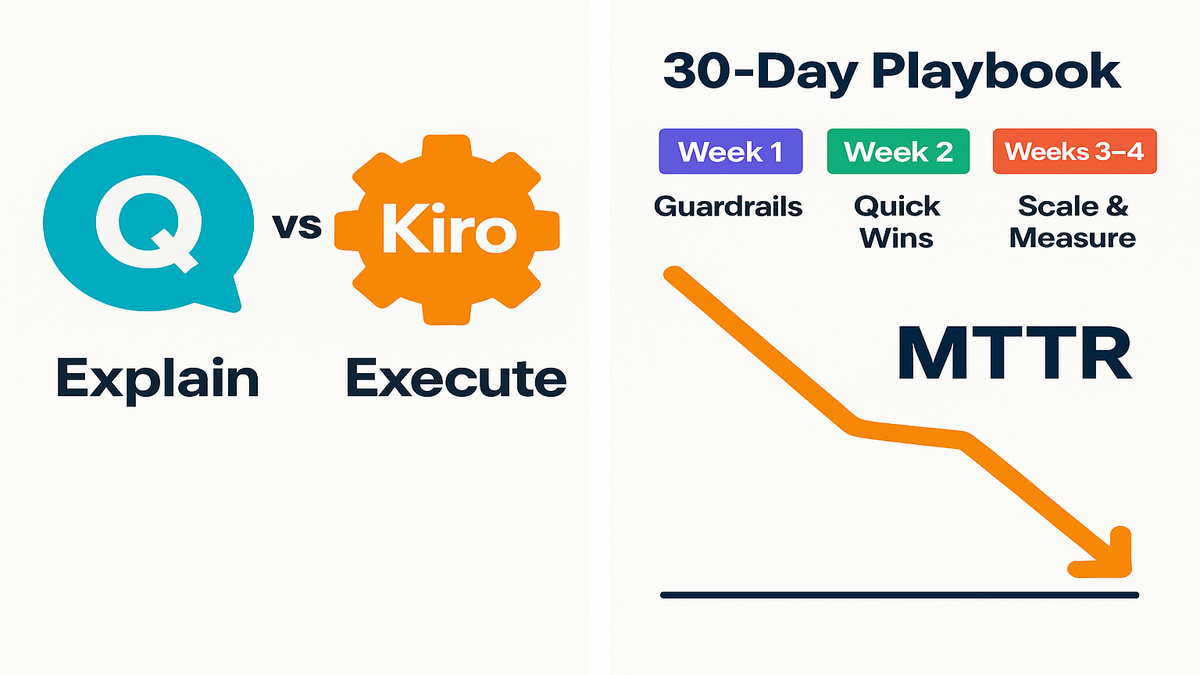
Amazon Q vs Kiro
Where Amazon Q shines
Amazon Q is AWS’s generative assistant for work. It answers questions, helps write code, and navigates docs and console context. It helps you think, plan, and create faster across business and developer workflows.
If you’re drafting a Terraform module, exploring an S3 policy, or summarizing CloudWatch logs, Q shines. It accelerates human-in-the-loop tasks, with strong context and content support.
Use Q to draft change plans, risk assessments, and runbook updates. It translates engineer-speak into stakeholder updates and meeting-ready summaries, without dashboard spelunking.
Where Kiro likely leads
Kiro, Amazon’s AI for cloud workflows, looks aimed at execution. Less “explain Kubernetes,” more “patch this nodegroup now, roll it out safely, and update the status page.” It does things in order, with approvals, like an orchestration brain.
So when you see “amazon q vs kiro,” think complementary tools. Q helps you understand and generate; Kiro helps you operate and automate.
How they work together
Imagine this loop. Q analyzes a log spike and guesses a memory leak. Kiro validates with metrics, scales instances, opens a ticket, and posts a retro template. Q then drafts a fix PR with unit tests. Different jobs, same outcome: faster resolution with accountability, for everyone.
Under the hood, Kiro follows your change management rules. Q handles the text-heavy work—plans, docs, and PR descriptions. Together, they turn tribal knowledge into repeatable, reinforced workflows.
Best practice: keep separation of duties clear and written down. Q can propose and document; Kiro can execute within pre-approved limits. Approvals stay human, with evidence attached to every change, always.
First 30 days with Kiro
Week 1 access and guardrails
- Define the blast radius for early tests and limits, clearly. Start in dev and staging, not production, obvious but worth saying. Create IAM roles that strictly scope Kiro’s powers, from day one.
- Write “golden path” policies: when Kiro can propose vs. auto-execute actions.
- Wire logging: CloudTrail + CloudWatch dashboards to track Kiro’s actions and anomalies.
- Clarify approvals: who clicks yes in prod, on-call, platform, or both?
Additions that help:
- Tag resources with ownership and environment to improve targeting and reporting.
- Document rollback steps for each allowed action, in detail, please. If a change fails, the path back is instant.
- Set change windows and maintenance policies, in advance, always. If it’s 2 a.m., allow only stabilizing actions.
Week 2 quick wins
- Incident warmups: allow Kiro to restart unhealthy ECS tasks or recycle pods based on health checks.
- Scaling policies: Kiro can adjust ASG or K8s HPA limits within defined ceilings.
- Hygiene tasks: rotate keys, clear stuck queues, fix drift on common configs.
- Documentation: Kiro posts to Slack/Teams with before/after details and runbook references.
Look for patterns:
- If dependencies are flaky, add backoff and retry playbooks immediately.
- If cache thrash appears, warm paths before shifting traffic over.
- If alarms are noisy, tighten thresholds and add correlation rules.
Weeks 3 to 4
- Add higher-stakes changes: controlled rollouts, canary restarts, feature-flag flips, carefully.
- Integrate with Systems Manager Incident Manager for paging and timelines.
- Define KPIs: MTTR, change failure rate, toil hours reclaimed, and approval latency.
- Run a game day to test everything under pressure, together. Let Kiro handle predefined failure modes; your team observes and tunes.
First-hand scenario time. You hit a 2 a.m. latency spike. Kiro correlates an RDS CPU surge with a new deploy. It rolls back to the previous task definition and warms the cache. It posts a full timeline and leaves a PR comment with a proposed config fix. You wake up to green graphs and a clear retro.
Measurement tips:
- Capture a pre-pilot baseline for MTTR and change failure rate.
- Track the percent of events auto-resolved vs. human-approved, each week.
- Watch approval latency—often the hidden drag on recovery times overall.
- Keep a weekly “toil ledger” so wins are visible to stakeholders.
Kiro questions answered
1.
What is Amazon Kiro
Amazon Kiro is a new AWS service mentioned in a launch roundup. It integrates generative AI to enhance cloud workflows, automate complex tasks, and assist in real time. The goal is AI-powered decisions and actions, aligned with AWS services and guardrails.
2.
Amazon Kiro launch date
As of today, AWS hasn’t announced a firm launch date. Expect updates via AWS What’s New, the AWS blog, and events like re:Invent. If you work in regulated environments, plan extra approvals time once GA hits.
3.
Kiro downloads
Kiro will likely be a managed AWS service, not a traditional download. If AWS ships an Amazon Kiro IDE extension, it would appear in VS Code or JetBrains marketplaces. Wait for official announcements and avoid third-party installers, please, online.
4.
Amazon Q vs Kiro
Amazon Q helps you understand, generate, and navigate across docs, code, and business data. Kiro focuses on operating and orchestrating actions in AWS with context and approvals. In practice, Q explains; Kiro executes, simply put.
5.
Security and data access
Expect standard AWS patterns: IAM-scoped permissions, CloudTrail auditing, and encryption in transit and at rest. You control what Kiro can see and do through policies. Review the shared responsibility model and service-specific security notes.
6.
Pricing
No public details yet, from AWS today. If it follows AWS norms, expect pay-as-you-go based on requests and steps. There may be model usage costs if it leverages Bedrock. Budget a pilot and measure ROI on toil reduced and MTTR improvements.
7.
Replace runbooks
Unlikely; it can operationalize them, pretty well. Keep runbooks as truth, then teach Kiro which ones run automatically. Some require approval, with verification steps to prove success.
8.
Test changes safely
Use staging environments, narrow IAM scopes, and synthetic loads to test actions. Add pre-checks and post-checks for health, error rates, and rollback paths. Game days turn edge cases into muscle memory over time.
Make your stack Kiro ready
- Inventory top 5 repetitive ops tasks you’d safely automate, today.
- Define IAM roles with least privilege for those tasks, precisely.
- Write “approve vs. auto-execute” rules per environment and team.
- Instrument CloudTrail and CloudWatch to trace actions, end-to-end.
- Document rollback paths and canary thresholds, for safety.
- Create a Slack/Teams channel for AI-generated change logs and alerts.
- Set KPIs: MTTR, approval latency, change failure rate, toil hours.
Pro tip: add consistent tagging so logs, metrics, and resources line up by service and owner. When an incident hits, clean metadata makes AI smarter and approvals faster.
Naming helps, too. Standardize action names like “stabilize-service,” “warm-cache,” and “rollback-taskdef,” everywhere. Consistency reduces cognitive load and makes audit trails easier to scan.
You’re on the verge of a new ops pattern: AI that acts, not just chats. If Kiro lands as positioned, you’ll codify judgment calls, speed safe changes, and reduce noisy toil. The winners won’t be teams that just try AI; they’ll wrap it with guardrails, telemetry, and measurement. Start by mapping two high-confidence workflows, define hard limits, and run a controlled pilot. In six weeks, you’ll know if Kiro is a novelty or your new default.
References
- Amazon Q product page
- Amazon Bedrock overview
- AWS Step Functions
- AWS Systems Manager (including Incident Manager)
- AWS Identity and Access Management (IAM)
- AWS CloudTrail
- AWS Shared Responsibility Model
- McKinsey (2023): The economic potential of generative AI
- GitHub (2022): Quantifying GitHub Copilot’s impact
- Amazon EventBridge
- Amazon CloudWatch
- AWS Config
- AWS Systems Manager Change Manager
- AWS Well-Architected Reliability Pillar
- Google SRE Book (Eliminating Toil)
- DORA Research (DevOps metrics)

