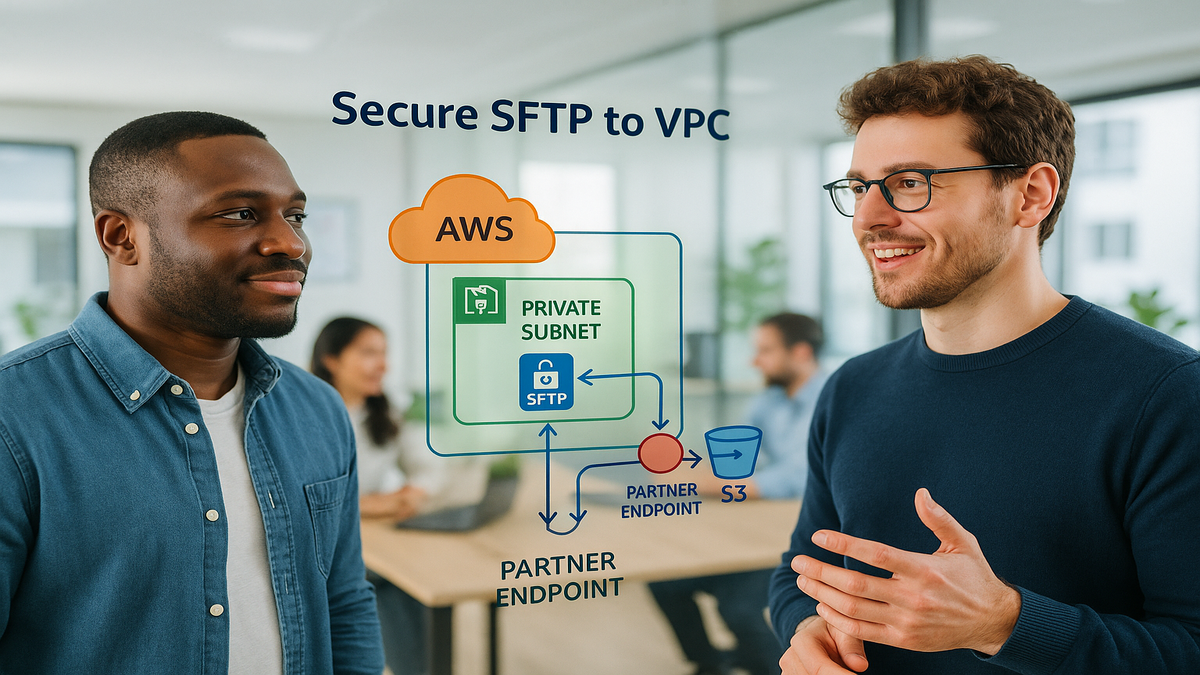
Secure SFTP to Any VPC with AWS Transfer
Jacob Heinz
AWS Transfer Family now lets SFTP and FTP connectors run inside your VPC.
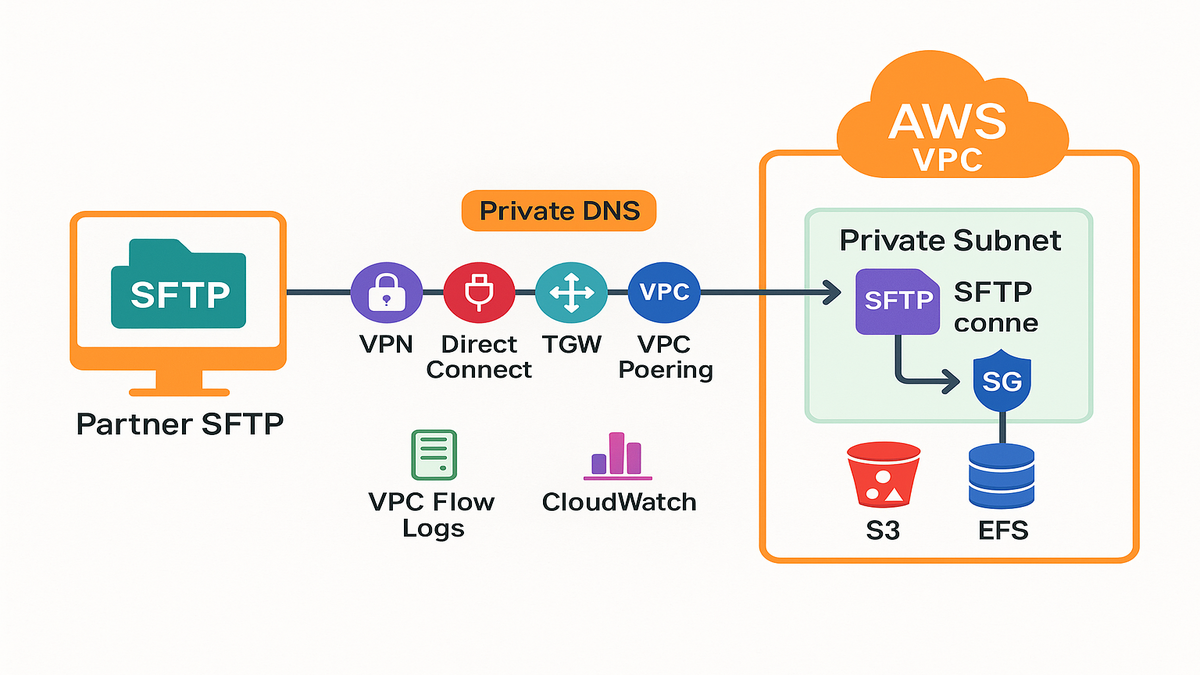
Traffic stays private over VPN, Direct Connect, Transit Gateway, or VPC peering.
No public internet exposure at all, which keeps the path private.
Key steps
- Place connectors in private subnets and lock down egress in security groups. Use TCP 22 for SFTP; for FTP include only the partner’s passive port range.
- Make sure private DNS resolves using Route 53 private hosted zones or Resolver forwarding. Set correct routing over VPN, DX, TGW, or VPC peering as needed.
- Use VPC endpoints to avoid NAT or an internet gateway entirely. S3 uses a gateway endpoint; Secrets Manager, CloudWatch, KMS, and STS use interface endpoints.
- Write to S3 or EFS with least-privilege IAM and clear policies. Store partner credentials and keys in AWS Secrets Manager for safe handling. Encrypt everything with SSE-KMS for keys and data at rest.
- Watch traffic with VPC Flow Logs and metrics with CloudWatch. Audit API operations end-to-end using CloudTrail for compliance and tracing.
Common fix
- setstat unsupported error occurs because S3 does not support POSIX attributes. Disable preserve timestamp and permissions settings in the SFTP client. Manage file permissions with IAM instead, not POSIX metadata at all.
Custom hostname
- Attach an ACM certificate and map a friendly DNS name. For example, sftp.example.com points to your Transfer Family server host. That makes partner onboarding cleaner and less confusing, which folks appreciate.
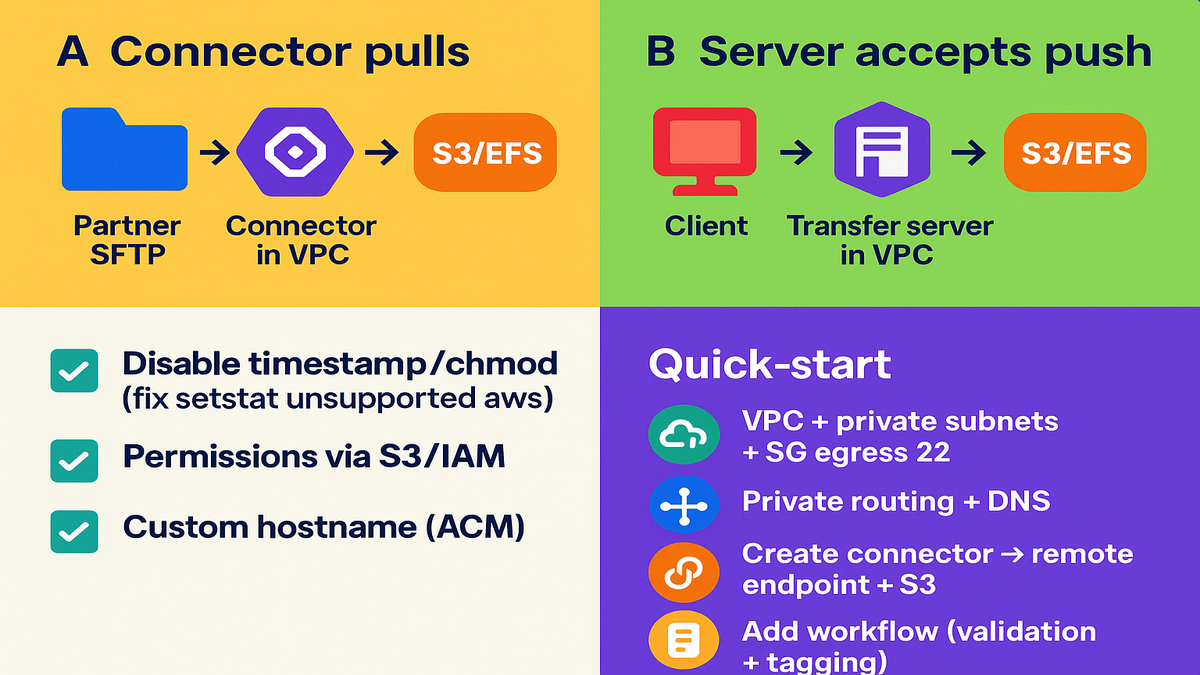
Quick start
1) Pick a VPC, private subnets, and a tight egress-only security group. 2) Configure private routing and DNS resolution to the partner endpoint. 3) Create a connector targeting the partner and an S3 destination. 4) Add a workflow for validation and tagging, simple and clear. 5) Test with a small file and review CloudWatch and VPC Flow Logs.