
Master SP-API Authorization And Prevent Costly Outages Now
Picture this. It’s month-end. Orders spike. Vendors refresh POs. Your integration throws a wall of 401s. Not because your code broke. Your API authorization lifecycle did. The token expired. Scopes drifted. Or your charge method lapsed. Silent killers. The worst part? They look normal until your warehouse texts, “Where are today’s orders?”
Good news: this is fixable. Amazon’s SP-API runs on OAuth 2.0. Do it right. Register cleanly. Link Vendor Central credentials correctly. Manage tokens with discipline. Keep your charge method valid. Then you stop firefighting and start shipping. You go from reactive to steady and boring. That’s exactly what you want when your business depends on those calls.
Here’s the playbook for rest API access authorization enhancements that actually move the needle. You’ll see why auth is not a sprint. It’s a lifecycle. A few guardrails can save your uptime, reputation, and weekend. We’ll map the SP-API flow. Sharpen your token hygiene. Lock down scopes. And set alerts so 401s and 403s yell early, not at 2 a.m.
TLDR
- Treat auth like a product: design, monitor, rotate, and review.
- Follow Amazon’s OAuth 2.0 flow: register developer, register app, link Vendor Central credentials, request scopes, handle tokens.
- Use Authorization: Bearer correctly; rotate and store tokens safely.
- Keep a valid charge method on file to avoid SP-API disruptions.
- Apply API security best practices: least privilege, RDT for sensitive data, secrets management, and monitoring.
Authorization Changes
Why this matters now
SP-API access is getting stricter, on purpose. Amazon wants you to manage the authorization lifecycle with rigor. Keep a valid charge method. Connect the right credentials to the right vendor groups. It’s not red tape. It’s risk management. Your win: fewer outages and cleaner audits.
It matters now because your integrations link to more systems. One sloppy scope or expired refresh token won’t just fail a call. It blocks downstream jobs. Inventory syncs. Invoice pushes. Shipping confirms. Think of authorization like a permission supply chain. A weak link breaks the flow.
The risk you cant ignore
When API authorization drifts, failure stays quiet. Refresh tokens expire softly. Scopes don’t match new endpoints. The card on file lapses. One tiny gap and your app flips from fine to blocked.
OWASP’s API Security Top 10 puts broken object-level authorization (BOLA) at API1. They call it “the most common API vulnerability.” That’s not theory. It’s the daily vector that turns routine requests into data leaks or ugly errors.
“Most common” is the key phrase. If your auth model is fuzzy, risk is not abstract. It’s inevitable. Broad scopes, sketchy token storage, brittle refresh flows. You don’t fix this with quick patches. You fix it with lifecycle thinking: plan, implement, monitor, rotate, and renew.
A real world pattern
- Week 1: You launch with correct scopes and a working refresh.
- Week 6: You add a new vendor group but don’t link credentials. This includes mapping scopes carefully to prevent overreach and strengthening api authorization: bearer handling.
- Week 8: Your charge method expires. Tokens still flow until renewal is forced. Then access dies on renewal.
- Week 9: Team scrambles, hotfixes, and adds a PM ticket called “rethink auth.”
You can skip the scramble with proper rest API access authorization enhancements from the start. Most teams aren’t “bad” at auth. They’re busy. Guardrails make busy safe.
“Broken object level authorization is the most common API vulnerability.” — OWASP API Security Top 10 (2023)
Map the SP API OAuth
Core steps to follow
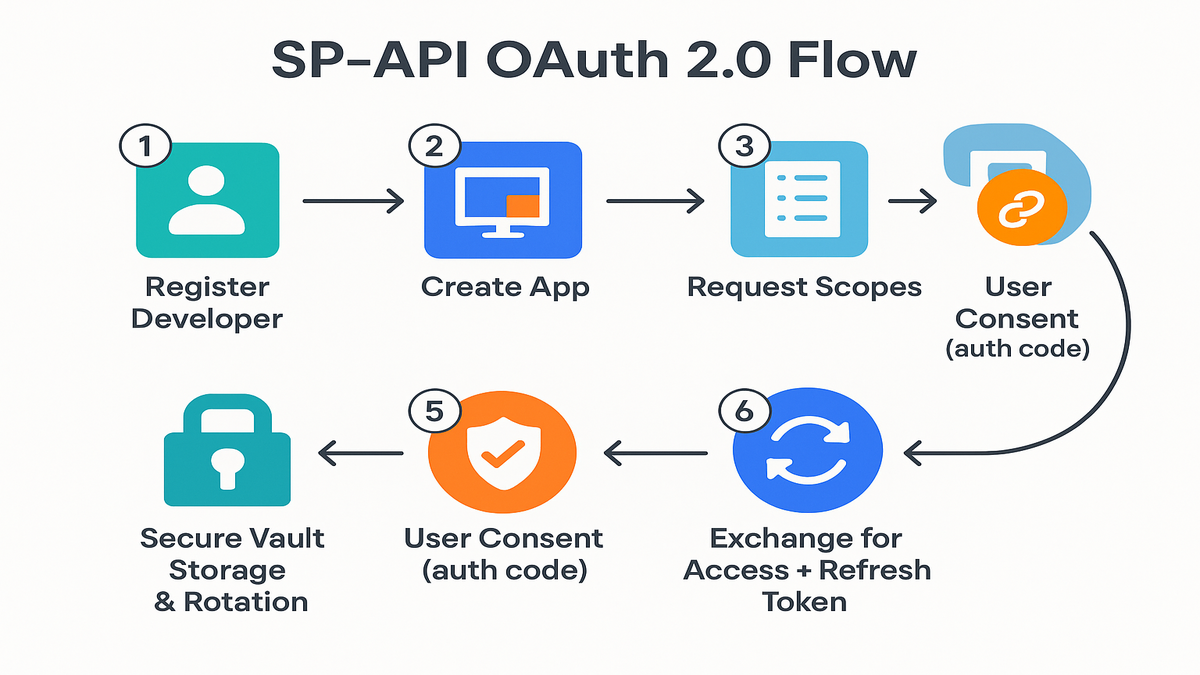
Amazon’s SP-API uses OAuth 2.0 for delegated access. The official flow is simple if you respect the details:
1) Register as an SP-API developer. 2) Create and configure your SP-API application. 3) Link the right Vendor Central credentials so your app accesses the correct vendor groups. 4) Implement OAuth 2.0 authorization code flow. 5) Request only the scopes you need; use Restricted Data Tokens (RDT) for sensitive endpoints. 6) Store and rotate tokens securely.
RFC 6749 says it well: “The OAuth 2.0 authorization framework enables a third-party application to obtain limited access to an HTTP service.” That’s your north star. Limited. Measured. Auditable.
API access authorization enhancements example
Here’s an outcome-driven path you can copy:
- You register your developer profile, then your app.
- You map endpoints to specific scopes. No wildcards.
- You link Vendor Central credentials to align with your vendor group.
- Your login page sends the user to Amazon’s consent screen.
- You capture the authorization code and exchange it for an access token plus refresh token.
- You store tokens in a vault with per-tenant encryption keys.
- You set rotation alarms before token expiry. Jobs rotate seamlessly with no user friction.
Now layer in a few practical decisions:
- Multi-tenant separation: Never share refresh tokens across tenants or vendor groups. One tenant, one set of secrets.
- Marketplace mapping: Keep a registry of marketplaces and the resources each tenant actually uses. Don’t request scopes “just in case.”
- Consent UX: Show a plain-language list of what access you’re asking for and why. This reduces consent fatigue and cuts support tickets later.
Pro tip
Treat scopes like firewall rules. Default deny, then allow only what’s required. Document every scope-to-endpoint reason in your repo.
“The OAuth 2.0 authorization framework enables a third-party application to obtain limited access to an HTTP service.” — IETF RFC 6749
Common pitfalls and fixes
- Scope drift: A team adds calls to a new endpoint but skips a scope review. Result: 403. Fix: PR template requires scope mapping and reviewer sign-off.
- Missing Vendor Central link: You call vendor endpoints without linking the correct vendor group. Fix: Add a preflight check that validates linkage before onboarding.
- Refresh race conditions: Two workers refresh the same token at once and stomp each other. Fix: Use a single-flight lock or lease to serialize refreshes per token.
- Clock skew: Your system clock drifts; tokens look not yet valid. Fix: NTP everywhere and a few seconds of grace in your validation logic.
Bearer tokens done right
Use Authorization Bearer correctly
Every call to SP-API resources should include api authorization: bearer in the HTTP Authorization header. That’s the minimum. The craft lives in how you manage those tokens.
RFC 6750 defines bearer tokens plainly: a token any party in possession can use. Translation: it’s cash. You protect it like cash.
“A bearer token is a security token with the property that any party in possession of the token (a ‘bearer’) can use the token.” — IETF RFC 6750
Rotation and expiry strategy
- Short lifetime: Respect Amazon’s token TTLs and rotate proactively.
- Refresh discipline: Automate the refresh flow; don’t wait till the last minute.
- Kill switches: Revoke tokens fast if credentials are compromised or roles change.
- Idempotent refresh: Only one refresh runs at a time; cache results to all callers.
- Backoff logic: If you hit 401 after refresh, pause and re-fetch once. Then fail loudly. Don’t loop forever.
Storage and transport hardening
- Vaults only: Store tokens in a secrets manager. AWS Secrets Manager or HashiCorp Vault work great. No env files in repos.
- Access boundaries: Per-tenant encryption keys. No shared secrets across customers.
- mTLS where allowed: Use TLS 1.2+ and pin chains where feasible.
- No logs: Redact tokens in logs, traces, tickets, and screenshots. Scrub before export.
- Memory hygiene: Zeroize token buffers when done. Don’t leave tokens in dumps.
Sensitive data use RDT
If you touch personal or financial seller data, use Restricted Data Tokens. They tighten access and time-box sensitive calls. That helps you follow api security best practices by default.
Design tip: Wrap RDT behind a tiny internal SDK. Callers use one function that requests an RDT, calls the endpoint, then destroys the token. Make the safe way the easy way.
Alerting that saves you
- Monitor 401/403 rates and latency.
- Alert on failed refresh attempts.
- Detect unusual scope usage, like a client calling a brand-new endpoint.
- Correlate with deploys: Mark dashboards with releases to spot auth regressions.
- Billing linkage: If 401s spike, show account charge-method status in the same view.
This is how api authentication and authorization methods go from implemented to resilient.
Need queryable logs and dashboards to catch 401/403 spikes and scope anomalies fast? Try Requery.
Keep your charge method alive
Why Amazon cares
Amazon needs a valid charge method on file for developers. If your charge method lapses, SP-API access can get disrupted. It’s not punitive. It’s part of the platform’s compliance model. The fix is simple. Keep a current card. Monitor expiry dates. Assign ownership for renewals.
What actually breaks
- Refresh flow fails at renewal checkpoints.
- Consent can’t complete for new authorizations.
- Certain endpoints may gate access until your account is in good standing.
The worst part? It often shows up as generic “unauthorized” behavior. Your logs say 401, but the root cause lives in billing. Devs chase ghost bugs while accounting holds the key.
Ownership and automation
- Owner: Make charge-method hygiene a named responsibility. Not just “finance’s problem.”
- Automation: Calendar reminders 60/30/7 days before card expiry.
- Health checks: Daily checks that your SP-API account is active and your developer profile is valid.
- Separation of duties: Finance updates the card. Engineering monitors status and alerts near renewal.
- Sandbox parity: If you use a sandbox, mirror production so renewals aren’t forgotten.
Vendor Central linking non optional
If you build for vendors, link Vendor Central credentials to the correct vendor groups. Access boundaries tie to those groups. Wrong link, wrong data, wrong dashboards.
“Use least privilege for every access decision.” — OWASP (Principle of least privilege)
Security practices that stick
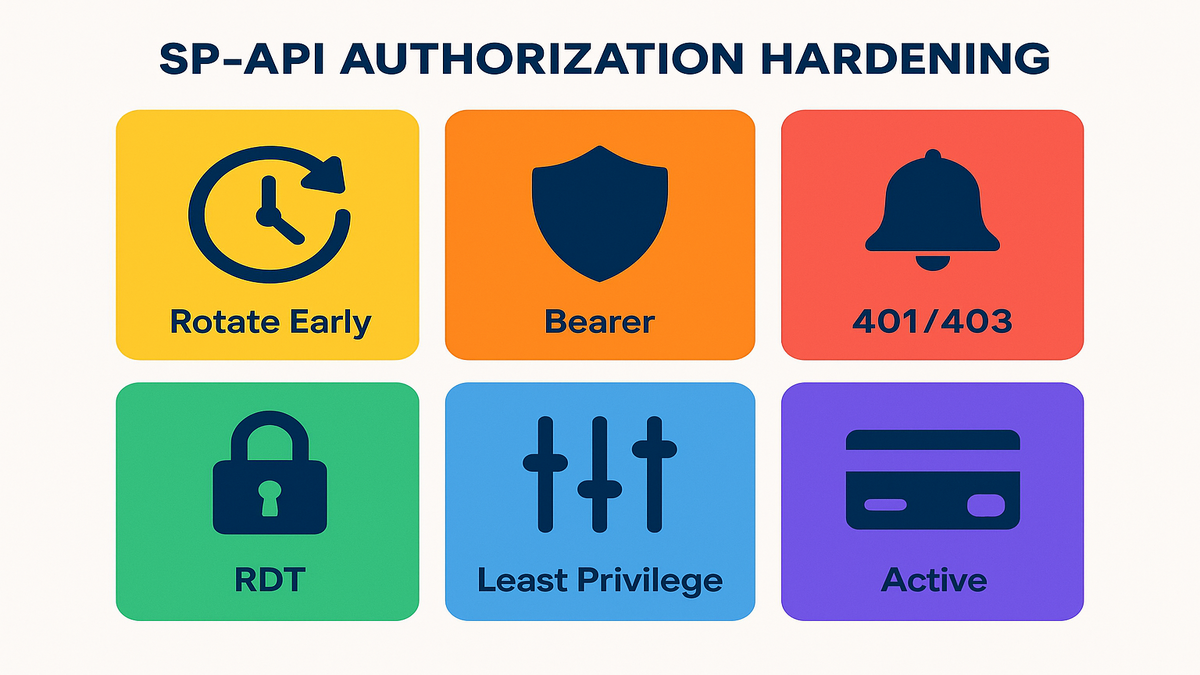
Build a minimum viable guardrail
- Least privilege scopes: Only request what your job needs.
- RDT for sensitive fields: Bake it in early.
- Deny-by-default: If a new endpoint appears, force a review before use.
- Preflight checks: Before enabling a tenant, verify scopes, vendor linkage, and billing status.
Secrets and key management
- Centralize secrets: Use a managed vault with rotation policies.
- No long-lived credentials: Prefer short-lived, auto-rotated tokens.
- Commit hooks: Scan for secrets in CI. Block merges on hits.
- Break-glass policy: Time-bound emergency access with audit logs.
Network telemetry and testing
- Allowlists: Lock down egress to SP-API domains and your IdP.
- Structured logging: Correlate 401/403 with token events and account status.
- Chaos tests: Simulate expired tokens, revoked scopes, and invalid charge methods.
- Integration SLOs: Set SLOs for auth freshness. Alert when breached.
People and process
- Two-person reviews for scope changes.
- Quarterly access reviews for vendor groups.
- Runbooks for token leaks and billing issues.
- Onboarding checklist: New engineer? Walk through OAuth flow, secrets handling, and the no-logging rule.
When you think “api authorization,” think lifecycle. Requirements → implementation → monitoring → rotation → review. That rhythm is your moat.
“Defense in depth is essential for reducing the attack surface.” — OWASP (General guidance)
Diagnose auth scope or billing
Use this quick flow when things fail. Keep it next to your on-call phone:
1) Check HTTP code:
- 401 after a deploy? Likely expired or invalid token, or broken refresh.
- 403 on a specific endpoint? Scope mismatch or missing vendor linkage. 2) Validate token freshness:
- Did a refresh happen recently? Was it successful? Any race conditions? 3) Compare scopes to endpoint:
- Did the endpoint change? Did your app add a call without a scope review? 4) Vendor Central linkage:
- Is the vendor group linked to your app and the right account? 5) Billing status:
- Is the charge method valid? Any recent declines or expirations? 6) Retry policy:
- Backoff properly. If one refresh fails, retry once. Then page a human.
Bonus: Add a “/health/authz” internal endpoint that checks token validity, scope coverage, vendor linkage, and charge-method standing. Run it every hour.
Practical examples to borrow
- Scope-to-endpoint ledger: Keep a small markdown file per service. List each endpoint you call and the scope that justifies it. PRs must update it.
- Token refresh microservice: Centralize refresh logic behind a stable API. All workers call it. It serializes refresh and returns cached results.
- Consent campaign: For legacy tenants, schedule a week to re-consent with the minimal scope set. You’ll find and prune unused access.
- Alert thresholds: Trigger an alert if 401s exceed a rolling threshold in 5 minutes. Or if refresh attempts fail twice in a row for any tenant.
- Tenant quarantine: If a tenant’s card expires or vendor link breaks, pause their jobs. Post a status event so your CSM can reach out.
Quick pulse check
- Authorization fails quietly. Design loud alerts for 401/403 spikes and failed refresh.
- Follow Amazon’s OAuth 2.0 flow exactly: developer registration, app setup, Vendor Central linking, scope discipline.
- Treat bearer tokens like cash: short-lived, rotated, vaulted.
- Keep a valid charge method to avoid avoidable disruptions.
- Embed least privilege, RDT, and secrets management as defaults.
FAQs That Clear Confusion Fast
What are these enhancements
They’re the concrete practices to harden SP-API access. Strict OAuth 2.0 flows, precise scopes, secure token storage, proactive rotation, Vendor Central credential linking for vendors, and a valid charge method to prevent outages.
Need OAuth for SP API
Yes. Amazon’s SP-API uses the OAuth 2.0 authorization code flow. You register as a developer, register your app, get user consent, then manage access and refresh tokens to call SP-API endpoints securely.
Authentication versus authorization
Authentication verifies who is acting, like a user or app. Authorization controls what they can do, like scopes and vendor groups. SP-API uses both. You authenticate via OAuth and authorize by granting narrow, specific scopes.
How to use bearer
Include the access token in the HTTP Authorization header as “Bearer
Need Restricted Data Tokens
Use RDT for sensitive data, like personal info. RDT narrows access and time-bounds calls. It aligns with api security best practices and reduces blast radius.
Why charge method matters
Amazon requires a valid charge method to keep your developer account in good standing. If it lapses, some auth and token operations can break. Monitor card expirations and assign ownership for renewals.
Prevent refresh token stampedes
Use a single-flight mechanism per token, like a mutex or lock. One worker refreshes. Others wait and reuse the new token.
Retry policy guidance
- 401: Try one refresh and one replay. If still 401, stop and alert.
- 403: Don’t retry blindly. Check scopes and vendor linkage.
- 429: Use exponential backoff with jitter. Respect headers.
Review scopes and access
Quarterly is a solid baseline. Tie reviews to a calendar, not memory. Include scope lists, vendor group memberships, and secret rotations.
Authorization hardening gameplan
- Register developer and app. Document scopes per endpoint.
- Link Vendor Central credentials to the correct vendor groups.
- Implement OAuth 2.0 authorization code flow with vaulted token storage.
- Enforce least privilege. Use RDT for sensitive endpoints.
- Automate token rotation. Alert on 401/403 and refresh failures.
- Keep a valid charge method. Set 60/30/7-day expiry reminders.
- Quarterly review: scopes, vendor groups, secrets, and runbooks.
- Add a preflight to onboarding: verify billing, scopes, vendor linkage, and consent before enabling jobs.
- Build a tiny internal SDK for tokens and RDT so teams use the same safe patterns.
Wrap up
Authorization is not a bolt-on. It’s a living system. Respect the lifecycle. Design scopes with intent. Automate rotation. Vault secrets. Monitor relentlessly. Keep your charge method current. You turn a fragile integration into durable infrastructure. The payoff is quiet. No late-night pages. No surprise 401s. No mystery outages. That silence is the sound of compounding reliability. Your future self will thank you.
Prefer not to rebuild all the guardrails yourself? Explore our Features for built-in token rotation, secrets vaulting, and health monitoring.
References
- Amazon SP-API: Authorization and Authentication
- Amazon SP-API: Registering as a Developer
- Amazon SP-API: Creating and Configuring an Application
- Amazon SP-API: Authorizing Applications for Vendors
- Amazon SP-API: Restricted Data Tokens (RDT)
- IETF RFC 6749: The OAuth 2.0 Authorization Framework
- IETF RFC 6750: OAuth 2.0 Bearer Token Usage
- OWASP API Security Top 10 (2023)
- OWASP API1: Broken Object Level Authorization

