
Take Control Of IAM Identity Center With CMKs

Jacob Heinz
|
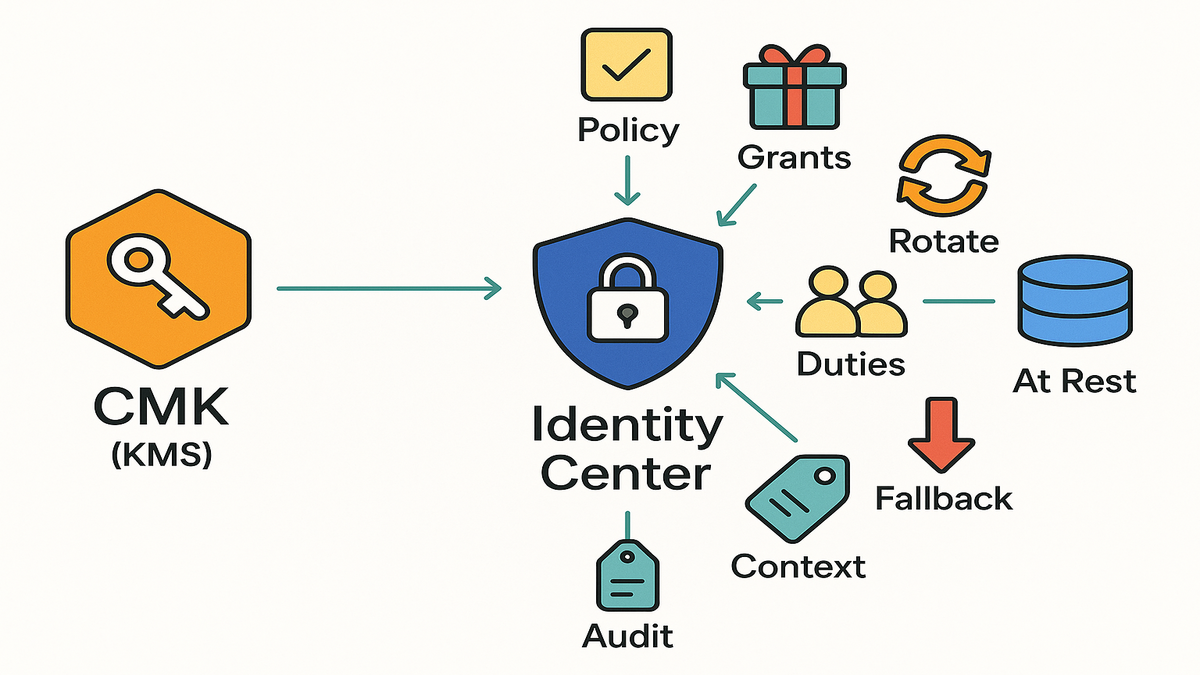
AWS IAM Identity Center (formerly AWS SSO) now supports encrypting user, group, and instance metadata at rest with your own customer-managed AWS KMS keys (CMKs).
Key takeaways
- You control key lifecycle, policies, rotation, and revocation.
- Encryption context ties decrypt operations to your specific Identity Center instance for stronger misuse protection.
- Switching to or between CMKs takes seconds; if permissions are misconfigured, the service auto-falls back to the previous key to protect availability and surfaces an error for admins.
- All KMS cryptographic calls are logged in AWS CloudTrail for audit.
- Identity Center remains free; standard AWS KMS charges apply.
Practical guidance
- Create a symmetric CMK in the same Region as your Identity Center organization instance.
- Use a tight key policy for admin access; delegate usage via grants to the Identity Center service roles.
- Enable key rotation; tag keys with owner/purpose/environment.
- After enabling in Identity Center settings (Manage encryption), smoke test sign-in, attribute CRUD, and account/app launches; verify KMS Encrypt/Decrypt in CloudTrail.
- Set alerts for unusual CMK usage; keep a break-glass role and deny risky actions like ScheduleKeyDeletion to most operators.
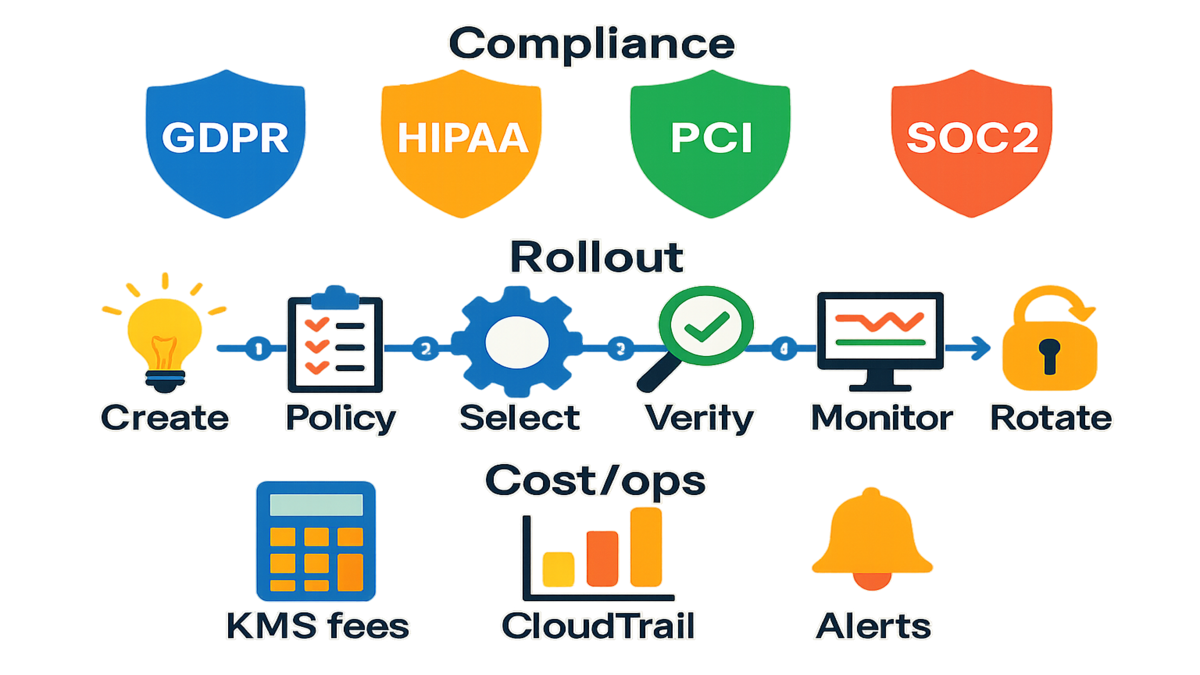
Who benefits most: regulated orgs (GDPR, HIPAA, PCI DSS, SOC 2), teams standardizing on CMKs, and enterprises requiring separation of duties between identity operations and key custodians.
In short: you keep the same Identity Center experience, gain full key governance and auditability, and can meet strict compliance requirements without disrupting SSO.

