
Lock Down Origins Fast: CloudFront mTLS Kills Shared Secrets
You probably have at least one origin hiding behind a shared secret. Maybe a custom header, an allowlist, or a brittle CI token. It works for a while, until it doesnt, and then chaos shows up. Stolen creds are still a top way in for breaches. Rotating those secrets hurts and always hits Friday night somehow. If you’ve ever hunted that header across lambdas, containers, and old pipelines, you know the vibe.
Here’s the flip you wanted all year, and it lands today. Amazon CloudFront now supports mutual TLS (mTLS) to your origins. Translation time, because this matters a lot right now today. CloudFront presents a client certificate to your backend on connect. Your backend only accepts connections from CloudFront distributions you explicitly trust. No shared secrets hiding in pipes or sticky notes anymore. No spray and pray headers that leak at the worst moment. Just strong, standard, certificate‑based authentication that maps to real identity. Your security people will sleep better, and future‑you won’t be stuck diffing mystery headers at 2 a.m.
This works across AWS origins like ALB, NLB, or API Gateway. It also works with your on‑prem boxes and third‑party CDNs used upstream. If you ship proprietary docs, private APIs, or licensed media, this helps a lot. Origin mTLS closes risks you never fully solved with one‑off headers. You get a cleaner security story, easier rotations, and a path that scales without duct tape. Because it uses standard TLS and x.509 under the hood. Audits get simpler, automation gets saner, and rollout is boring in a good way.
TLDR
- CloudFront now supports mutual TLS for origins, so no more shared secrets between edge and origin.
- You can enable mTLS per-origin across AWS, on-prem, and third-party backends.
- Stronger than custom headers or IP allowlists; certificate rotation is predictable and automatable.
- Viewer mTLS isn’t native in CloudFront; use API Gateway or NLB if you need it.
- Use CloudFront Functions to route traffic to origins that require different client certs.
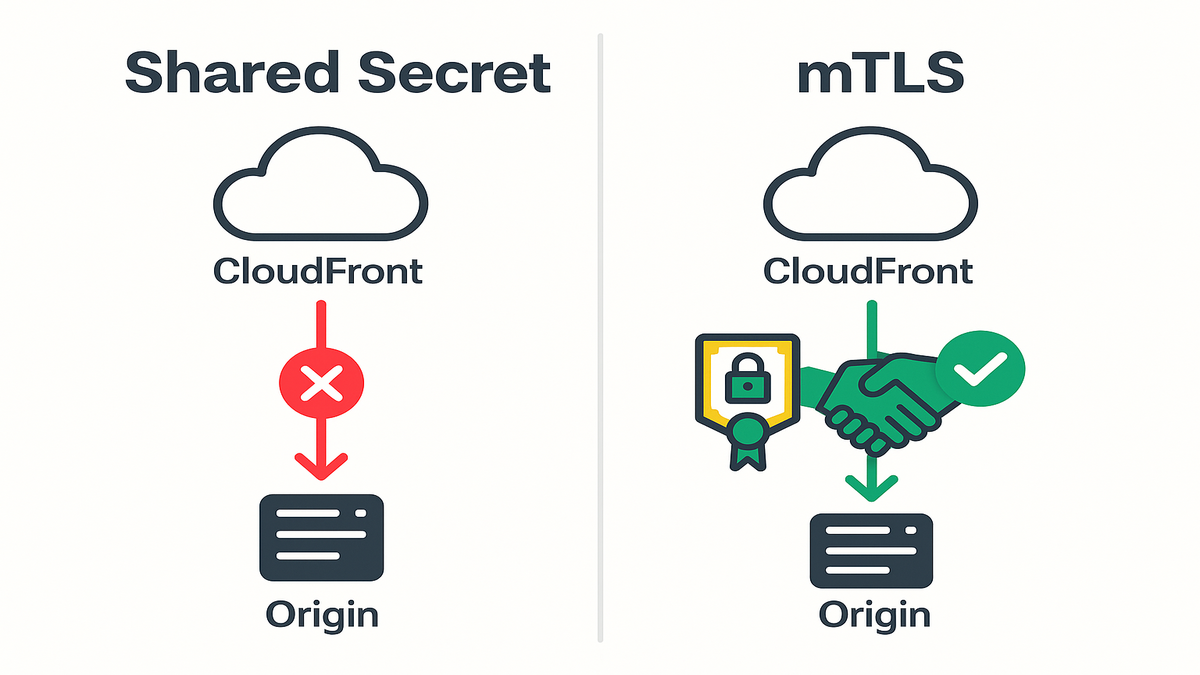
Why your origin leaks
Shared secret drift is real
If your origin trusts CloudFront with a secret header, that leaks sooner or later. Anyone who learns that header can hit your backend directly. Rotations run late, copies hide in old pipelines, and exceptions become permanent. That’s attack surface you truly dont need.
Even with IP allowlists, you’re juggling moving targets and weird rules. Think dynamic ranges, multi‑CDN failovers, and old contractor entries that never vanished. Traffic analyzers and error pages leak just enough to help attackers probe. One bad staging endpoint can become a backdoor into production.
mTLS flips trust to identity
With origin mTLS on CloudFront, your backend validates a client certificate first. No cert, no handshake, and no request at all ever. You move from knowing a password to proving exact identity. This is identity enforced right at the transport layer boundary.
mTLS rides inside the TLS handshake, so checks happen before HTTP. Your app stack never even sees a request without a valid cert. You can trust the chain from CA to intermediate to client cert. Verify expiration and add revocation checks when you need them. You’re not hoping a proxy adds a header anymore. You now enforce identity with math, not vibes or luck.
Why it matters now
- Credential misuse is still a leading breach vector, per Verizon DBIR 2024. Moving off shared secrets shrinks your blast radius.
- Compliance teams love standards; TLS and x.509 are battle-tested, auditable, and automatable.
- Rotations become hygiene, not chaos, because certificates have lifetimes; renewals become calendar events, not incident calls.
- Least privilege gets easier to express: one client cert per origin or trust domain, segmented behaviors, and clean isolation.
Here’s a first-hand example that landed well for a fintech. They streamed private portfolio docs and replaced origin headers with CloudFront mTLS. The origin was an ALB, and the change went smooth. Outcome was zero secret sprawl and automated ACM rotation. They also got a cleaner audit trail across runs weekly. Their ops lead said it best: we removed a class of 3am tickets.
Pro tip you should keep pinned on the wall forever. mTLS doesn’t replace auth in your app at all ever. It gates who can connect, before your app allows any actions. Think defense in depth, not a full replacement.
How origin mTLS works
The handshake in one breath
- Your origin is configured to require client certificates and trusts a specific CA, public or private.
- CloudFront, for the configured origin, presents a client certificate during the TLS handshake.
- The origin validates the cert chain against its trust store and checks revocation and expiry.
- Only then does HTTP start; no cert, no handshake, and no party.
Behind the scenes, the origin uses SNI and normal TLS flows. It can validate SAN fields and enforce policies like allowed issuers. If you trust a CA, you can roll leaf certs smoothly. You won’t re-add every single thumbprint to the origin trust list.
Certificates without tears
You manage server and client certs with ACM or your PKI. Because it’s standard mTLS, your origin can run almost anywhere. Think ALB or NLB, on‑prem NGINX, or another CDN as an upstream. That makes enabling origin mTLS on CloudFront a repeatable pattern. Not a one-off snowflake build that breaks later under load.
- Prefer short-lived certs like ninety days and automation over long-lived static certs.
- Name and tag certs clearly; include the CloudFront distribution ID and origin name.
- If you run a private CA, publish CRLs and or enable OCSP to support revocation checks.
- Keep chains lean; extra intermediates add size and verification time without security gain.
Safer than headers
- Custom headers: trivial to leak, and hard to rotate globally.
- IP allowlists: brittle with dynamic ranges, tricky across multi-CDN, and break on failover.
- mTLS: standard crypto, deterministic verification, and clear lifecycle for teams.
Another real example you might like from healthcare land today. A healthcare API trusted a secret header and an IP range. Two vendor changes later, both controls drifted in weird ways. They moved to mTLS, and the origin accepted only CloudFront’s client cert. A fallback read-only origin required a different cert for separation. Clean separation, and no brittle lists to debug later again.
Here’s what mTLS won’t fix for you. Open direct-to-origin endpoints still need to be closed for good. Misrouted DNS and overbroad IAM on origin servers still bite. It narrows the pipe, but you must still lock the door. And you need to watch the hallway with logs and alerts.
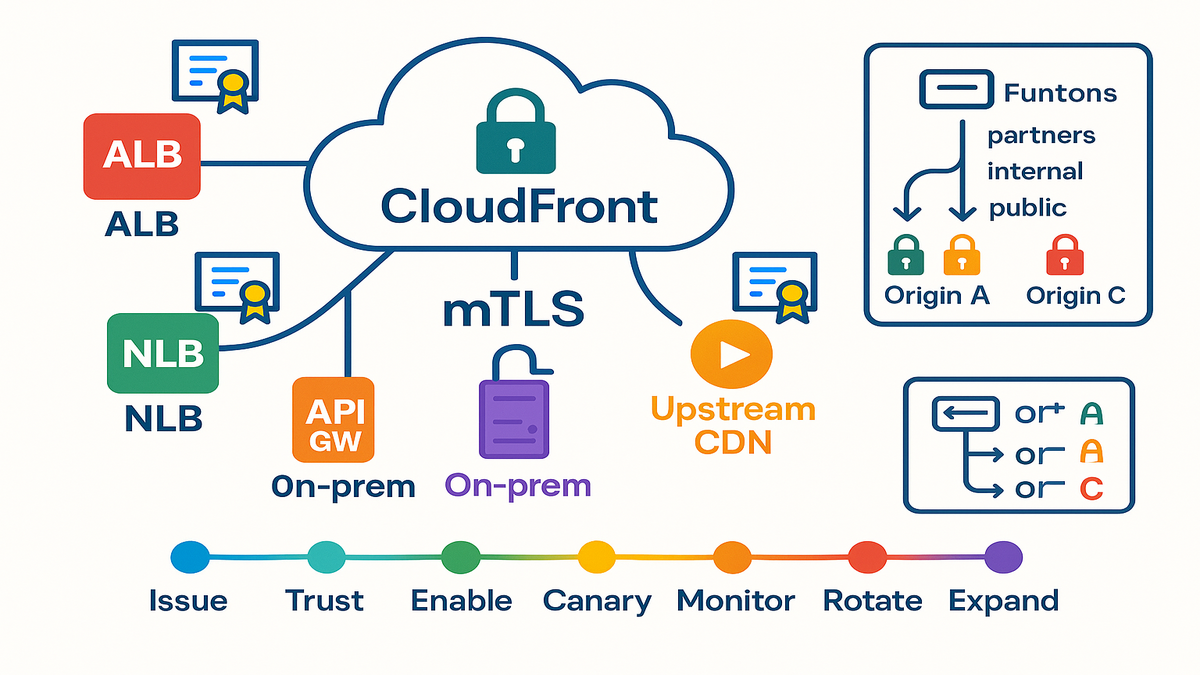
Architectures you can ship today
AWS origins
- Application Load Balancer: terminate TLS and validate client certs upstream of your app. Good for HTTP(S) with WAF, path routing, and standard web workloads.
- Network Load Balancer: for ultra-low latency and client auth at L4 with TLS, use NLB’s TLS listener and trust store.
- API Gateway: if you need viewer mTLS to your API, use its mutual TLS on custom domains. CloudFront doesn’t support viewer mTLS natively today at the edge.
Design tips
- Keep one client cert per trust domain, like internal versus partner versus public-read origins.
- Use different origins in a single distribution whenever policies diverge.
- Don’t mix viewer mTLS needs with origin mTLS; delegate viewer cert auth to API Gateway or NLB, then let CloudFront cache safely.
On premises and hybrid
Your on‑prem NGINX or Envoy can require client certs from CloudFront. Drop your enterprise CA chain into the trust store on servers. This shines for proprietary data, licensing servers, or intranet content via edge caching.
- NGINX: configure a trust bundle, enable client verification, and set a strict verification depth.
- Envoy: define a downstream TLS context with trusted CAs and require client certs.
- Rotate by swapping the trusted CA or adding a new intermediate during a transition window.
Third party CDNs
Running multi-CDN or origin-of-origin right now for real, I know. Configure the upstream to require CloudFront’s client certificate. This enforces only your CloudFront distributions can connect upstream. You still keep your current caching and PoPs strategy intact.
- Verify your upstream supports client cert auth on origin fetch connections.
- Use per-CDN client certs to isolate incidents and simplify blast-radius analysis.
Real world story from a media company running hot events too. They fronted a legacy CDN with CloudFront for cost control and smarter keys. They made the legacy CDN accept only CloudFront’s client cert upstream. Result was no rogue direct hits to pricey legacy endpoints. Traffic shaping stayed smooth during live events and spikes too.
Deploy mTLS without breaking stuff
Setup flow
1) Issue a client certificate via ACM or your PKI for CloudFront. It will be presented to a specific origin. 2) Configure your origin to require and validate client certs against the issuing CA or trust bundle. 3) Update your CloudFront distribution’s origin settings to use mutual TLS for the origin with CloudFront. 4) Roll out with a canary path or origin group; monitor 4xx and 5xx and TLS alerts.
Add a pre-flight test before you ship changes this week. Hit the origin directly with a throwaway cert and confirm trust store behavior. Then deny direct public access before going live with CloudFront. You do not want to leave a weird bypass open.
Rotations that feel boring
- Short lifetimes: ninety-day certs force good hygiene and reduce risk.
- Staged deploys: attach the new client cert to a second origin; flip traffic gradually using weighted behaviors.
- Automated renewals: use ACM for managed rotation where possible and automation for custom PKI.
- Drift checks: periodically confirm the origin trust store matches the intended CA set, with no surprise intermediates.
Gotcha to avoid so you dont break prod at midnight. Do not rotate a leaf cert without updating any pinned intermediate. Keep a runbook that lists pinned versus inferred trust anchors.
Observability and rollback
- Log TLS handshakes and cert validation errors at the origin, including NGINX, Envoy, and ALB or NLB logs.
- Build synthetic checks that verify both certificate presence and validity.
- Keep an emergency non-mTLS origin behind tight IP allowlists for break-glass, then remove it once stable.
- Alert on certificate expiration at 30, 14, 7, 3, and 1 days through your monitoring stack.
First-hand example from a SaaS analytics vendor who ships fast. They added mTLS behind an internal path first, like /internal/. After two weeks of clean metrics, they expanded to /api/ safely. Zero downtime and zero guesswork during the rollout for them.
Policy performance and Functions
Policy who can talk
mTLS lets you encode trust one origin at a time. If Team A should not call Team B, issue distinct client certs. Keep separate origins and map them to the right behaviors. Your origin only trusts the CA or leaf that matches.
- Use one CA per environment, like dev, stage, and prod, to reduce cross-env risk.
- Tag certs and origins consistently so audits are one query away.
- For partners, set expiry windows that match contract terms.
Performance real world overhead
TLS handshakes add cost, but the impact is usually minimal. Between CloudFront and a regional origin, keep-alives smooth it out. For most APIs and assets, latency deltas hide under network noise. If you’re super latency sensitive, pin origins regionally and trim chains.
- Favor HTTP keep-alive and tune your origin connection pools.
- Keep certificate chains short and keys modern, like ECDSA where supported, to reduce CPU.
- Measure before and after with p50 and p95 latency and error rates; confirm it’s just a rounding error.
CloudFront Functions smart routing
You can use CloudFront Functions to steer requests to different origins. Route by path, cookie, or header, with each origin using its client cert. That’s how you implement origin mTLS with CloudFront Functions cleanly. Example maps that just work:
- /partners/* → Origin A with Partner CA
- /internal/* → Origin B with Corporate CA
- /public/* → Origin C without mTLS (read‑only)
Viewer mTLS note you should know cold for real folks. Viewer mTLS is not supported natively at the CloudFront edge. If you need the viewer client cert, use API Gateway mTLS instead. Or terminate on NLB with client auth and keep caching upstream. CloudFront will not carry the viewer client cert through today.
First-hand example from a B2B platform with enterprise tenants inside. They mapped tenants to per-tenant origins using a CloudFront Function. Each tenant origin required a tenant-scoped client certificate. Isolation improved and the incident blast radius shrank a lot.
Bonus routing ideas
- Send write traffic to origins that enforce mTLS; route read-only cached assets to public origins.
- Gate experimental features behind origins with a separate client cert so rollbacks are trivial.
Quick pulse check
- You’ll eliminate fragile origin secrets and painful IP gymnastics from your stack.
- You’ll tie access to identity, using certificates, not possession like headers.
- You’ll get cleaner rotations, clearer audits, and fewer late-night rollbacks for teams.
- You can segment origins by trust domains using CloudFront Functions cleanly.
- Viewer mTLS? Use API Gateway or NLB; CloudFront handles origin mTLS only.
FAQ Straight answers
mTLS replace Origin Access Control
No, mTLS does not replace Origin Access Control for S3. OAC uses SigV4 to connect CloudFront to S3 without public buckets. mTLS for CloudFront targets TLS-authenticated custom origins like ALB or NLB. Use OAC for S3 and mTLS for custom HTTPS origins.
viewer mTLS with CloudFront
Not natively at the edge right now for viewer certs. CloudFront terminates TLS and doesn’t expose viewer certificates upstream anywhere. If you must do viewer certs, use API Gateway mutual TLS. Or use an NLB with client-auth enabled in front instead.
Rotate the client certificate
Attach a new client cert to a staging origin for testing. Validate the trust chain on the backend before any traffic moves. Shift traffic using weighted behaviors or path-based routing patterns. After validation, retire the old cert cleanly and quickly please. Keep cert lifetimes short and automate renewals by default always.
Work with on prem servers
Yes, this works great with on‑prem servers too for mTLS. Any TLS-terminating server that validates client certs is fine here. Think NGINX, Envoy, HAProxy, or even IIS in shops today. Import your CA chain into the trust store and enforce client auth. Enable mTLS on the matching CloudFront origin settings as configured.
Use another CDN upstream
Treat that CDN as a custom origin that requires CloudFront’s client cert. Only CloudFront with the trusted certificate can connect upstream reliably. This pairs nicely with multi-CDN and migration strategies too honestly.
Performance hit
There’s a small handshake cost that connection reuse usually hides. In practice, origin mTLS overhead is usually negligible. Network variance and cache misses dominate more than handshakes. Keep chains short and origins regional for best results always.
Trust a CA or pin
Trust a dedicated CA per trust domain for smoother rotations. You can issue new leaves without changing the origin at all. Pin a leaf only when you need extreme control and manual rotations.
Handle multi account multi region
Use a per-account CA hierarchy or per-region intermediates for trust. Distribute trust bundles through your config management system at scale. Scope client certs to the distribution and origin pair they serve.
Use WAF and auth headers
Yes, keep those controls in place alongside mTLS for safety. mTLS is a front-door identity check, not full app auth. Keep WAF for layer seven protections, rate limits, and bot controls. Keep app auth like tokens and cookies for user permissions.
Seven step mTLS rollout
1) Inventory origins and mark which require origin mTLS with CloudFront.
- Prioritize high-value APIs and any origin protected by shared headers. 2) Issue client certs via ACM or your PKI; document lifetimes and owners.
- One cert per origin trust domain; tag owner, rotation window, and distribution ID. 3) Configure your origin to require client-auth and load the right trust store.
- Test with a known-good client cert; verify rejection on missing or invalid certs. 4) Enable mTLS on the CloudFront origin; canary with a narrow path.
- Start with internal or admin paths; monitor logs and expand gradually. 5) Monitor TLS errors, origin 4xx and 5xx, and handshake metrics.
- Watch for expired intermediates, mismatched CAs, and SNI quirks. 6) Automate renewals and plan rotations thirty days before expiry minimum.
- Add alerts at 30, 14, and 7 days; bake rotation into sprints. 7) Expand coverage path by path, then deprecate headers and IP allowlists.
- Remove the old controls to avoid shadow paths and confusion.
You can secure an origin with a header, or secure it with math. mTLS makes the math option the default going forward everywhere. Turn on origin mTLS with CloudFront and get verifiable identity. You trade vibe-based security for clear, strong, provable checks instead. You’ll reduce credential risk and simplify audits across teams fast. You’ll set up clean, automated rotations without drama each quarter. If you waited for a standard way to lock down content, here it is. Start with one high-value origin, watch logs, then expand everywhere. Until secrets are a weird memory you laugh about later.
Infrastructure rule of thumb: every secret you don’t create is one you’ll never leak.
One more thing before you go, please remember this always. When in doubt, ship the smallest slice, measure, and iterate. Security that ships beats perfect security stuck on a whiteboard.
References
- Amazon CloudFront Developer Guide (service overview)
- AWS Certificate Manager (ACM) overview
- AWS Private Certificate Authority (ACM PCA)
- TLS listeners for Network Load Balancer (client auth capable)
- Amazon API Gateway mutual TLS
- CloudFront Functions
- NGINX client certificate verification
- Envoy client certificate authentication
- HAProxy SSL client authentication
- Verizon Data Breach Investigations Report (DBIR) 2024
- CloudFront private content controls (OAI/OAC context)
- RFC 8446: The Transport Layer Security (TLS) Protocol Version 1.3
- RFC 5280: Internet X.509 Public Key Infrastructure Certificate and CRL Profile
- OWASP TLS Client Authentication

