
Today’s AWS Headlines: Cloud, AI, Security, Sustainability Wins
If you’re doom-scrolling breaking headlines today, here’s the thing you shouldn’t miss. AWS quietly shipped updates that hit your budget, security, and ESG report, all at once.
You’ve read enough hot takes this week. This is the opposite: simple moves you can use inside your AWS account without a committee. Think levers that move in days, not quarters, plus shortcuts other teams already tested.
Everyone’s chasing local news today and usa news today headlines. But if you run apps in the cloud, AWS moves can save real dollars and real headaches. This week’s signals: stronger community programs, a security push for AWS re:Inforce 2025, and a louder sustainability beat tied to the Customer Carbon Footprint Tool (CCFT) expansion.
And budgets and audits don’t care about feelings, so timing matters. These updates match how teams ship: better defaults, cleaner reporting, and fewer sharp edges when incidents hit at 2 a.m. This is about as close to free compounding as it gets.
Translation: less noise, more compounding gains if you move early. While breaking news Trump might dominate your feed, the real impact on your stack is here. Faster incident response, clearer emissions math for leadership, and a growing talent pipeline via AWS Community Days. Let’s turn the news today in the world of cloud into outcomes by Friday.
Pick one thread—community, security, or sustainability—and you’ll see lift across all three. That’s the quiet cheat code. Small moves here unlock budget, reduce risk, and keep auditors happy without slowing devs.
- TL;DR
- AWS is doubling down on communities, security training, and sustainability.
- re:Inforce 2025 will spotlight identity, detection, and builder-first security.
- CCFT expansions make emissions reporting easier for audits and CSRD.
- Community Days = free knowledge arbitrage and recruiting upside.
- Net: expect tighter governance, clearer ESG reporting, and faster rollouts.

What Actually Shipped
And Why You Care
Community momentum that compounds
AWS Community Days keep scaling worldwide—grassroots, builder-led meetups with real architectures, cost wins, and postmortems. The value is one-sided in your favor. You grab battle-tested patterns and recruiter eyeballs without the vendor gloss. Trying to cut EC2 or EKS bills? You’ll meet folks who did it last quarter and will hand you their playbook.
Practical example: you leave with three Terraform modules, a talk on Graviton migrations, and a direct intro to a security engineer who automated IAM guardrails at a 100+ account org. That’s a quarter of trial-and-error packed into a Saturday.
If you haven’t been, here’s the move. Show up with a specific question and a tiny demo of your setup. Sanitized screenshots are fine. Ask, “What would you do different?” You’ll get tactical advice—naming, tagging discipline, FinOps dashboards, IAM layouts—you can ship next sprint. Bonus: hallway chats teach you what not to ship.
You can also treat Community Days like recruiting, without the recruiter. Share a real cost or reliability win, and you’ll get inbound from builders who care about the same problems. That’s a talent pipeline without a job posting.
Security energy ahead of
reInforce 2025
AWS re:Inforce is where hands-on security training meets deep product dives. Expect heavy focus on identity, detection, data protection, and incident response. The big picture is the same. Security is still “job zero” at AWS, and the event pushes the shared responsibility model into daily muscle memory.
If you map to NIST CSF or prep for SOC 2, this is where you pressure-test with the people who build and break these systems. One day of labs can cut weeks off your roadmap.
Show up with a gap list: stale IAM roles, open access patterns, noisy alerts, unclear runbooks. Use labs and chalk talks to pressure-test your fixes. Ask presenters, “What’s the simplest default that blocks 80% of identity risks?” You’ll leave with a priority backlog. Short-lived credentials, task-based roles, and automated containment for the highest-confidence detections.
The win isn’t only education; it’s alignment. Security leaders, platform engineers, and app teams leave speaking the same language and sharing a clear “done.” That’s how security becomes a feature, not a blocker.
Sustainability signal not virtue signaling
AWS keeps expanding the Customer Carbon Footprint Tool (CCFT), with clearer emissions data tied to your actual usage. This isn’t for feel-good dashboards. EU CSRD and board-level ESG asks are real. CCFT helps reconcile scope 2/3 questions and shows how regions and instance types change your footprint.
A 451 Research study found moving workloads to AWS can cut carbon versus typical enterprise data centers. Higher server use and cleaner energy mixes help a lot. That’s not theory; it’s a lever you can pull.
How this helps in real life: finance needs defensible numbers; engineering needs knobs to turn. CCFT gives both. Baseline emissions, model moves like “shift this service to Graviton in Region X,” then show cost-to-carbon tradeoffs like you compare instance families. That turns ESG from a slide into a sprint item.
If your company reports under CSRD, clarity matters. You’ll need audit-ready math, transparent assumptions, and a repeatable way to tie compute usage to emissions by month and region. CCFT becomes the source of truth you can explain to auditors without a climate PhD.
Why These AWS Moves
Change Your Roadmap
Cost control risk reduction
- Cost: Community Days feel like free R&D. You’ll find blueprints for right-sizing compute, using Spot without pain, and adopting Graviton to shave 20–40% on CPU-bound workloads.
- Risk: The average data breach cost hit roughly $4.88M in 2024, per IBM. Invest in identity, detection, and incident response training. It pays back the day you catch a privilege escalation in minutes, not hours.
- Talent: Your best engineers want to learn. Reinvesting in community and events is retention dressed up as training.
Run the math. If a Graviton migration saves 25% on a $80k/month workload, that’s $240k/year back to your budget. That’s before the performance-per-watt gain. If tighter identity stops one medium-impact incident, you probably covered a year of training and tools. And the talent flywheel—engineers shipping with better defaults—compounds into speed.
and talent pick three
Security is a product decision
If your sprint board doesn’t reflect AWS’s security momentum, you’ll pay later. Translate re:Inforce guidance into defaults. Tighter IAM boundaries, encryption everywhere, detection-as-code, and prebuilt runbooks for incidents. You’ll ship faster when guardrails make the secure path the easy path.
Make it boring on purpose. Define a paved path with:
- Identity: short-lived, role-based access tied to tasks; auto key rotation; human access via federated SSO.
- Data: encryption everywhere by default; simple key patterns devs don’t need to think about.
- Telemetry: CloudTrail and VPC Flow Logs on; GuardDuty watching; alerts routed to an actual owner.
- Response: runbooks as automation; clear severities; a muscle-memory game day, every quarter.
Measure it like product health. Track MTTD, MTTR, high-confidence alerts auto-resolved, and risky permissions removed per sprint. Security becomes an accelerant when it cuts decision fatigue.
not just a policy
Sustainability is now a
With CSRD hitting more companies, emissions math isn’t optional. CCFT gives you defensible numbers tied to usage. That turns ESG from a hallway debate into an input for engineering. Region choice, instance type, and placement that balance latency, cost, and carbon. The right dashboard can save you a painful Q4 audit.
Treat carbon like any budget line. Put cost and carbon side by side in the same dashboards. Build guardrails. Prefer regions and instance families that hit performance with lower carbon intensity, and document exceptions. When policy is clear and defaults are smart, compliance follows naturally.
hard requirement
Quick Pulse Check
Whats Worth Your Attention
- Community Days are underestimated career and roadmap accelerators—copy working patterns shamelessly.
- re:Inforce 2025 is your deadline to lock in identity and detection upgrades.
- CCFT expansion makes ESG reporting ingestible for finance and compliance teams.
- Costs fall when sustainability, security, and architecture align well.
- Headlines are noisy; these are quiet compounding advantages.
If you’re resource-constrained, sequence your energy. Identity first, then detection, then emissions dashboards. Identity shuts doors attackers try first; detection buys time; dashboards buy credibility and budget.
The Backstory
How AWSs Flywheel Works Now
The sustainability tailwind
Amazon stated a goal to power operations with 100% renewable energy by 2025. For you, that means a cleaner baseline each year. Combine that tailwind with your choices—Graviton, managed services, higher utilization—and you turn sustainability into margin. CCFT then gives you the receipts.
Real-world framing: you migrate a batch analytics job to Graviton-based instances and a more efficient region. You get lower compute cost, better performance-per-watt, and cleaner accounting for the board deck. Not bad for a one-week tweak.
Zoom out. Many teams find easy wins in CPU-bound services, nightly jobs, and stateless microservices. These are easier to port to Graviton, easier to right-size, and easier to schedule when renewables or cost curves are favorable. Start where the blast radius is small and the savings obvious, then scale.
Security as everyday ergonomics
The shared responsibility model never changed. AWS secures the cloud; you secure what you build in it. What changed is the ergonomics. Identity wants least privilege by default. Detection wants broad telemetry. Response wants codified playbooks, not war-room improv. re:Inforce lets you stress-test all this before your next audit.
A practical example: encode a deny-all, allow-by-exception IAM stance in reusable modules. Layer Organizations service control policies. Wire GuardDuty findings to automated containment. It’s not fancy—this is table stakes now.
Your north star: reduce toil. Use Access Analyzer to spot overbroad permissions. Standardize a small set of role templates. Gate production access through break-glass workflows with auto expiry. Fewer bespoke paths mean fewer 3 a.m. surprises.
Community as the derisking layer
Community Days and user groups are your de-risking layer. You trade stories and learn which managed features are ready, and which beta flags to avoid. The payback is speed. Fewer dead ends, quicker migrations, better on-call.
And yes, even if you mostly track usa news today headlines, the best roadmap “news” still comes from folks who shipped something hard last week.
A tiny networking script that works. Lead with your problem, not your title. “We’re seeing 30% idle CPU on EKS nodes; how are you packing workloads?” People love puzzles. Take notes, swap info, and schedule a follow-up. That’s how hallway chats become production fixes.
What To Watch Next
Practical Bets
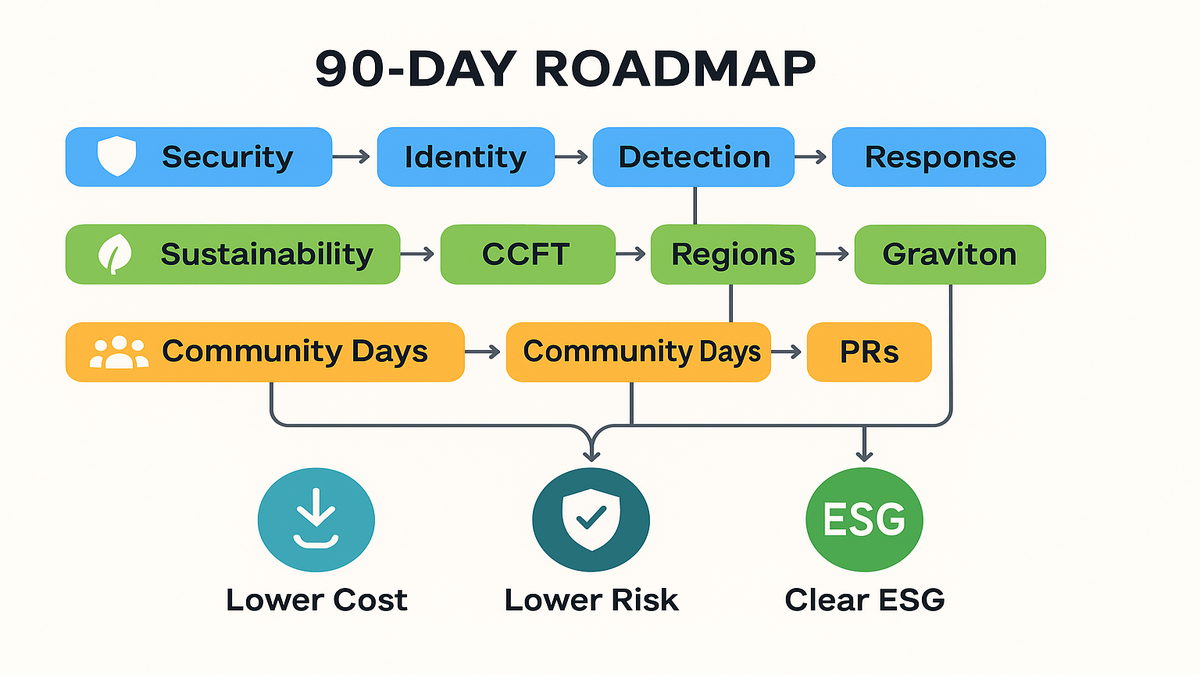
For The Next 90 Days
Security
- Identity: push to least privilege and short-lived credentials. Map roles to tasks, not humans.
- Detection: expand GuardDuty coverage, tune signal-to-noise, and auto-remediate high-confidence events.
- Response: practice. Run a game day. Fix friction. Good response feels boring because it’s scripted.
Regulatory pressure isn’t slowing. Translate NIST guidance into your backlog, and make security part of delivery, not a quarterly scare.
Operationalize with a simple weekly loop:
- Review top risky permissions and remove or scope them.
- Tune one noisy alert and add one automated remediation.
- Run a 30-minute drill on a single failure mode. Ship one improvement.
Sustainability
move from slideware to dashboards
- CCFT: wire cost and carbon views together so finance and eng speak the same language.
- Regions and instances: evaluate regions with a sustainability lens alongside latency and redundancy needs.
- Quick wins: target batch jobs and CPU-bound services for Graviton moves; quantify cost and carbon.
Your mini roadmap:
- Baseline: pull 12 months of CCFT and cost data; list top 10 services by spend and emissions.
- Model: simulate two changes—region shift or instance shift—and capture impact on dollars and carbon.
- Decide: publish a one-page RFC with the change and the KPI it will move.
Community
ship faster by standing on
others shoulders
- Attend one Community Day with a specific problem in hand.
- Book a recap with your team that same week.
- Turn takeaways into PRs for your internal platform repo. Learning is nice; pull requests are better.
And yes, if you need local news today, your nearest Community Day might be down the street.
Bonus move: propose a lightning talk on your before and after. Sharing buys feedback and future collaborators for your next migration.
FAQs
Your Most Pressing Questions Answered
Q: What exactly is AWS re:Inforce 2025? A: It’s AWS’s dedicated security conference with deep-dive sessions, hands-on labs, and best practices across identity, detection, data protection, and incident response. If you’re mapping to NIST CSF or prepping for SOC 2/ISO 27001, it’s the place to sharpen your program with practitioner feedback.
Expect lots of architecture patterns and “here’s how we broke it” stories. Show up with your gaps and leave with a backlog.
Q: How does the AWS Customer Carbon Footprint Tool (CCFT) help me? A: CCFT ties your AWS usage to estimated emissions so you can report, compare, and plan. It’s especially useful for CSRD-aligned reporting and board-level ESG talks. The practical win: model choices like region and instance type and see cost and carbon.
It also gives finance a single source for audit-ready numbers and engineering a clear set of dials to turn. That closes the loop between policy and practice.
Q: Are AWS Community Days worth the time for engineers? A: Yes. They’re practitioner-run, so you get real architectures, cost optimizations, and postmortems—plus a hiring pipeline. Treat them like free R&D. Attend with a problem, leave with working patterns and code you can adapt.
Pro tip: bring your tagging strategy or CI/CD pipeline examples and ask three people to critique it. You’ll get better at the basics fast.
Q: How do I balance security speed with developer velocity? A: Build security as defaults, not gates. Reusable IAM modules, paved paths for encryption, detection-as-code, and prebuilt incident runbooks let teams move fast safely. Measure friction. If the secure path isn’t the easiest, fix the path.
Automate approvals where possible, time-box human access, and publish a decision log. Transparency reduces shadow workarounds.
Q: Is sustainability actually material to my AWS bill? A: Directly, your bill is dollars. Indirectly, sustainability drives cost and risk wins. Higher efficiency with Graviton, smarter region choices, and less audit churn. Cleaner architectures often cost less and are easier to defend to finance.
Think of it like a design constraint that improves maintainability, like reliability did a decade ago.
Q: Where should I track AWS news without getting overwhelmed by breaking news headlines today? A: Start with AWS event pages like re:Inforce, official blogs, and your nearest Community Day page. Pair with one or two trusted analysts for quarterly context. Curate hard—signal beats volume.
Set a monthly 30-minute review and update your backlog with only items that move cost, risk, or velocity.
Your 7 Day Plan
To Turn News Into Outcomes
- Day 1: pick one priority—security, sustainability, or cost. Declare the metric you’ll move.
- Day 2: book one Community Day or user group, plus one re:Inforce track to follow.
- Day 3: baseline CCFT and cost dashboards; align with finance.
- Day 4: implement a least-privilege IAM module in one workload.
- Day 5: run a mini game day; document fixes.
- Day 6: identify one Graviton migration candidate; estimate savings.
- Day 7: share outcomes internally; lock a 30‑day follow-up.
You don’t need a big bang to win. You need compounding weekly reps.
The takeaway: not all headlines are equal. In a week of noisy feeds, AWS’s quiet updates offer edge you can bank. Security muscle memory, credible sustainability math, and faster learning loops via community. None of this needs a re-architecture; it needs focus. Pick one lever—identity, detection, or emissions reporting—ship a proof this week, and you’ll feel the compounding by next quarter.
References
- AWS re:Inforce official site
- AWS Customer Carbon Footprint Tool
- AWS Shared Responsibility Model
- AWS Community Day program
- AWS Sustainability hub
- IBM Cost of a Data Breach Report 2024
- 451 Research (S&P Global) — The Carbon Reduction Opportunity of Moving to AWS (whitepaper)
- Canalys — Global cloud market Q2 2024
- European Commission — Corporate Sustainability Reporting Directive (CSRD)
- AWS Graviton — Price/Performance Overview
- AWS IAM Best Practices
- Amazon — On path to power operations with 100% renewable energy by 2025
- NIST Cybersecurity Framework 2.0
- Amazon GuardDuty — Service overview
- AWS Well-Architected Framework Security Pillar

