
Top Amazon Linux 2023 highlights to harden your cloud
You’re not paid to babysit servers. You’re paid to ship. But when your OS image drifts, patching turns into whack-a-mole. Then CVEs pile up, and stress climbs fast. Someone asks, “Why is this still on Amazon Linux 2?” You sigh.
Here’s the fix: Amazon Linux 2023. It’s the latest Amazon Linux for cloud workloads, built for real teams. You get predictable releases, long-term support, and hardened defaults. So you focus on features, not firefighting or weird edge cases.
Want the fast path? Release date, GitHub, downloads, even the ISO question. It’s all below, nice and tidy. Want the why, not just the what? You’ll get a clear playbook. Roll AL2023 into your stack without wrecking your velocity.
Think of it like a reset button for base images. Fewer surprises. Cleaner builds. A simple, shared foundation. Your OS layer gets boring in the right ways. That’s the point. Your roadmap moves faster, and your pager finally quiets down.
And yes, AWS is still shipping. Serverless keeps improving. Load balancing gets smarter. Cloud ops feels cleaner. Pair that with AL2023, and your foundation gets boring, in the best way.
TLDR
- Amazon Linux 2023 focuses on security, stability, and long-term support.
- GA launched in March 2023 with a predictable cadence and an LTS window.
- Download via EC2 AMIs or container images; source code lives on GitHub.
- No official ISO download today; use AMIs, containers, or VM images instead.
- Quarterly updates keep you current without surprise breakage in your stack.
- Strong fit alongside ongoing AWS serverless and load balancing upgrades.
Essentials you care about AL2023
Security first cloud design
Amazon Linux 2023 (AL2023) is built for modern cloud workloads. Lean packages, tighter defaults, and reproducible, deterministic builds. You’re not wrangling a random community spin anymore. You’re standardizing on an OS tuned for EC2 and containers.
Expert quote you can ship: “Amazon Linux 2023 provides a secure, stable, and high-performance execution environment to develop and run your applications.” That’s straight from AWS, and it’s the north star for AL2023.
Under the hood, the big win is consistency. Your base image isn’t a stream of surprise upgrades anymore. It’s curated and predictable, which helps your supply chain story. Cleaner dependency graphs, easier SBOM generation, and fewer unknowns in prod. You also get better compatibility across EC2, ECS, and EKS. Standardize your Dockerfiles on the 2023 base, and life gets easier.
Predictable release cadence LTS
AL2023 is designed for planning, not surprises. You get a predictable cadence with quarterly updates and long-term support. Lock your base images, pass audits, and standardize across teams. Translation: fewer emergency OS sprints and calmer change windows.
In practice, that cadence lets you schedule patch windows reliably. Bake new golden images every quarter, then move them dev → stage → prod. For regulated environments, this is gold and saves headaches. Auditors love known-good baselines with a clear update rhythm. Teams love not getting dragged into surprise rebuilds midweek.
Where to get it
- EC2 AMIs: Available broadly; spin up in minutes from the console.
- Containers: Pull the official image at public.ecr.aws/amazonlinux/amazonlinux:2023 (see ECR Public Gallery).
- Source: Packages and build specs live on the Amazon Linux org on GitHub.
Stuck on a mix of base images? AL2023 helps you consolidate cleanly. You’ll simplify patching and reduce mental load across teams.
Add one note on images: pin by digest for containers in prod. Also document the AMI ID used for each release. That tiny bit of discipline saves hours when reproducing or rolling back.
Why this OS move pays off for you
Stability that speeds you up
Stability isn’t about moving slow. It’s about removing chaos. With AL2023’s predictable updates and curated repos, chaos drops. Fewer “works on laptop, fails in prod” moments. That’s real peace. You get consistent pipelines, cleaner SBOMs, and fewer late-night rollbacks.
It also standardizes your developer experience across the org. One baseline means shared Dockerfiles and shared CI templates. Fewer “where did this come from?” mysteries clogging reviews. New engineers onboard faster, and SREs aren’t detectives anymore. When the quarterly patch lands, you roll forward with confidence. No gambling on emergency fixes during a busy Wednesday.
Security that scales with org
Smaller, hardened images mean a smaller attack surface by default. Pair that with AWS-native tools like Systems Manager Patch Manager. Add Inspector for image scanning and CloudWatch for drift detection. AL2023 helps centralize vulnerability management with less patch whiplash. You’ll have more confidence shipping on Fridays, which feels nice.
Security teams also get traceability as a real feature. Known base images, known repos, and a steady, mapped cadence. Set up image scanning on push and block deploys on critical CVEs. Keep your roadmap moving while staying inside policy guardrails. Pro tip: treat your base OS like an application. Version it, scan it, promote it, and never “just patch in prod.”
Cost and ops wins
When every team uses the same baseline, you cut duplicated work. No more bespoke images and random upgrade paths across squads. It’s easier to standardize CI/CD and share base Dockerfiles. You can templatize Terraform or CloudFormation modules quickly. Your SREs will thank you when the patch dashboard turns green.
You also squeeze more out of automation with less variance. Runbooks and scripts don’t fork endlessly for edge cases. Run times get faster, and change failure rates drop a bit. Your toil metrics look better. Boring suddenly equals efficient.
Download and install
EC2 and Parameter Store
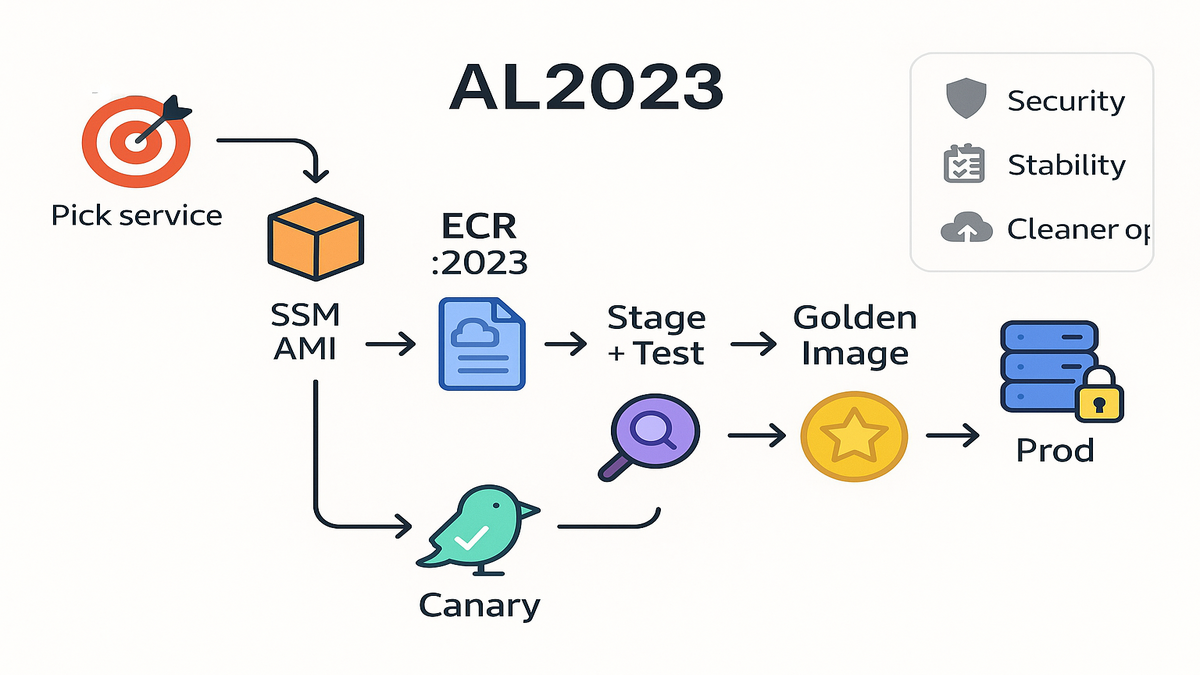
On EC2, use the console or Systems Manager public parameters. Fetch the latest AL2023 AMI IDs programmatically without guesswork. This keeps builds deterministic and avoids hardcoding those AMI IDs.
Most teams wrap this in a tiny helper script or function. Query SSM Parameter Store for the latest AL2023 AMI automatically. Tag it in your build system and pass it into launch templates. Combine with EC2 Image Builder or Packer for easy rebakes. You get a one-button path to rebake base images each quarter.
Containers the fastest on ramp
Using containers? Pull from ECR Public: public.ecr.aws/amazonlinux/amazonlinux (use the 2023 tag). It’s a clean baseline for multi-arch images across x86 and Arm. Works great with ECS, EKS, or straight Docker on your laptop.
Two practical tips:
- Pin by digest for prod promotions, so the “2023” tag doesn’t drift.
- Bake quarterly: when AL2023 updates land, rebuild, scan, and promote.
ISO download heres the deal
Looking for “amazon linux 2023 iso download” today? No luck, sorry. As of now, AWS does not publish a bootable ISO for AL2023. Instead, use these supported paths for your workflows:
- EC2 AMIs (cloud-native and simple)
- Official container images (great for CI/CD and microservices)
- Vendor or VM images where available, or build with Packer
This model keeps the distribution focused on cloud-first workflows.
Need a lab or on-prem test environment anyway? You have options. Many teams export AMIs to VMDK or VHD for testing. Some build from the container image as a rootfs for experiments. But the smoother path is testing in EC2 where the OS is native. Your telemetry, IAM roles, and controls are already there and trusted.
PDF docs and GitHub
You won’t find an official “amazon linux 2023 highlights pdf” handout. But the Amazon Linux 2023 User Guide is fully documented online. Use the PDF option on the docs page if you need something portable. For source and package specs, start at the Amazon Linux org on GitHub.
The GitHub org is useful beyond curiosity or browsing. Need to explain package provenance to an auditor? It’s all there. Compare spec changes across releases from a clean, central source. Link it in your internal wiki under “Base Image Reference.”
Release timing and update
Release date at a glance
Amazon Linux 2023 hit General Availability in March 2023. Since then, AWS ships quarterly updates on security and reliability. Everything stays predictable for infra teams planning ahead.
Still on Amazon Linux 2? Treat that GA date like a starting pistol. The longer you wait, the more one-off patches build up. They’ll get thrown away during migration anyway, which is frustrating. Move a small service first and codify the pattern carefully.
Amazon Linux 2024 isnt
You’ll see searches for “amazon linux 2024,” but there’s no separate major. AL2023 is the current major, and 2024 brought quarterly updates under it. The year-based naming gives clarity without yearly replatform panic.
That naming also helps your non-technical stakeholders track changes. Say, “we’re standardizing on Amazon Linux 2023 with quarterly updates.” It sets clear expectations for when changes land and how they’re controlled.
Update discipline that wont wreck
AL2023’s cadence is your friend and not your foe. Plan patch windows around quarterly cycles and bake on schedule. Bake updates into golden AMIs or containers, then roll forward. Keep a small canary fleet to catch regressions early every time. Lock dev, stage, and prod in a clean, controlled progression. Predictable ops beats heroics, every single time.
Set these guardrails:
- Ring deployments: canary → 10% → 50% → 100%, with timeboxed observation.
- Rollback plan: the previous golden AMI or digest is one click away.
- Telemetry: health checks plus error budgets, so you know when to pause.
- Freeze windows: don’t stack OS updates with big feature launches.
Upgrading from Amazon Linux 2
There’s no magic in-place upgrade from Amazon Linux 2 to 2023. The clean path is new AL2023 images and real testing. Validate your workloads, then cut over carefully. Yes, it’s extra work, but it pays down years of drift. You’ll end with a shared, standardized base across teams.
A simple migration checklist:
- Inventory: list services by criticality and dependency risk clearly.
- Pick a pilot: start with a low-risk service to test the pipeline.
- Rebuild: create an AL2023-based container or AMI and run tests.
- Scan: run security scans and fix any build-time vulnerabilities.
- Shadow or canary: run both images and compare metrics honestly.
- Cutover: promote when error rates and performance match SLOs.
- Rinse and repeat: templatize for the next batch of services.
Pro tip: use feature flags or traffic mirroring to validate behavior. You can test without switching every user in a single shot.
AWS momentum serverless ops
Serverless keeps compounding
AWS keeps shipping features and performance gains across Lambda and eventing. Build tooling is smoother, and cold starts keep shrinking over time. The effect is smaller cold-starts and simpler event pipes altogether. CI/CD for packaging functions gets nicer and faster. Pair that with AL2023-based containers for consistency everywhere.
Running a hybrid of Lambda and container services together? Standardize on AL2023 images for container-based tasks right now. Your dependencies stay aligned across batch, services, and jobs. That symmetry simplifies utility layers, CI steps, and security policies.
Load balancing smarter by default
Elastic Load Balancing keeps getting smarter across features and routing. Better protocol support, security modernizations, and cleaner defaults. Running gRPC behind ALB or high-throughput TCP behind NLB? Aligning on AL2023 keeps TLS stacks and userland libraries consistent.
Consistency matters a lot in real production systems. TLS configs, cipher suites, and CA bundles stay in sync. That reduces hard-to-debug handshake issues that waste hours. You’ll be ready for new ALB or NLB features faster too. Your userland is current and predictable across all services.
Cloud ops gets cleaner
Systems Manager, Inspector, and CloudWatch have matured nicely. Patching, drift detection, and inventory work better with a standard OS. Moving to AL2023 reduces variance and boosts automation effectiveness. Less yak-shaving, more buttons that actually do things on time.
You’ll feel the quiet productivity win within one quarter. Patch Tuesdays become patch Tuesdays again, not multi-week projects. Compliance reports read like a checklist instead of a long novel.
Quick pulse check
- AL2023 equals security, stability, and predictable updates you can trust.
- GA since March 2023; quarterly refreshes keep you current safely.
- Use EC2 AMIs or ECR Public containers; source lives on GitHub.
- No official ISO today; focus on cloud-native images instead.
- Standardize now to simplify patching, audits, and CI/CD pipelines.
FAQ everything people keep Slacking
When was Amazon Linux 2023
Amazon Linux 2023 hit General Availability in March 2023. Since then, AWS continues quarterly updates focused on security and stability. There’s long-term support to keep enterprise teams very comfortable.
Where download Amazon Linux 2023
- EC2: Launch via console or use Systems Manager public parameters for AMI IDs.
- Containers: Pull from ECR Public at public.ecr.aws/amazonlinux/amazonlinux (use the 2023 tag).
- Source: Explore packages and specs under the Amazon Linux org on GitHub.
amazon linux 2023 highlights pdf
There isn’t a separate “highlights” PDF at the moment. But the official User Guide is online with a PDF download option. Grab it on the docs page if you need an offline copy.
Amazon Linux 2023 ISO download
No. AWS does not publish a bootable ISO for AL2023. Use EC2 AMIs, official container images, or vendor or VM images instead. Those paths work for on-prem or lab setups with fewer hassles.
Amazon Linux 2024 release
No separate major release exists by that name. AL2023 remains the current major with 2024 quarterly updates under it. The cadence is designed for predictability and long-term support.
Upgrade from Amazon Linux 2
Not recommended and not supported as a one-click path today. Best practice is creating new AL2023 images and testing compatibility. Then migrate incrementally without breaking your production setups.
Manage AMI IDs and tags
Use Systems Manager public parameters to resolve the latest AMI at build time. Then freeze that ID in your golden images for predictability. For containers, promote by digest, not only by tag, to avoid drift. Document both in your release notes for clean traceability.
Right patching rhythm
Align with the quarterly AL2023 updates for sane planning. Bake a new golden AMI or container when updates land. Push it through dev and staging with your normal gates. Flip to prod once telemetry looks clean and stable. Smaller changes more often beats big-bang pain every time.
Keep audits simple
Stick to one baseline with AL2023 across your environments. Automate scanning on image build and at deploy time. Keep a short paper trail for each release and environment. Base image version, AMI ID or digest, scan reports, and approvals. When asked which systems use which image, answer from a dashboard. Not from a spreadsheet that’s always out of date.
Launch Amazon Linux 2023
- Pick a target workload, a low-risk service, for your first rollout.
- Pull public.ecr.aws/amazonlinux/amazonlinux:2023 and rebuild your container.
- For EC2, fetch the current AL2023 AMI via SSM public parameters.
- Stand up a staging environment and run integration and security scans.
- Bake a golden AMI or container and promote through canary, then prod.
- Document the base image and lock it in your CI/CD templates.
Then layer in day-2 operations:
- Add alarms for drift; if an instance deviates, page the right team.
- Rotate keys and certs alongside quarterly OS updates to bundle work.
- Track CVEs against base image versions for hotfix or quarterly decisions.
Here’s the punchline: boring infrastructure is a feature. When your OS layer is predictable and supported, you ship faster. Amazon Linux 2023 gives you that in a clean, practical way. Security-centric defaults and a sane update cadence, with broad tooling support. Across EC2 and containers, it just works like you’d expect. Pair it with serverless and load balancing improvements from AWS. You get a stack that’s faster to build on and easier to keep clean.
If you’ve been waiting for the right moment to standardize, this is it. Move a small service, codify the pattern, then scale the migration. Your future self, and your pager, will be very happy indeed.
References
- Amazon Linux 2023 product page
- What is Amazon Linux? (AL2023 User Guide)
- AWS News Blog — Announcing Amazon Linux 2023
- Amazon Linux on ECR Public (official container images)
- Amazon Linux organization on GitHub
- Systems Manager public parameters for Amazon Linux AMIs
- AWS Systems Manager Patch Manager
- Amazon Inspector — container image scanning
- EC2 Image Builder (for golden AMIs)
- Elastic Load Balancing — product overview
- AWS Lambda — product overview
2005: Netflix wanted $50M from Blockbuster. Blockbuster laughed. 2025: You’re deciding between ship fast or patch forever. Pick boring foundations early; the compounding is real.

